-
What is the difference between Encryption and Hashing?
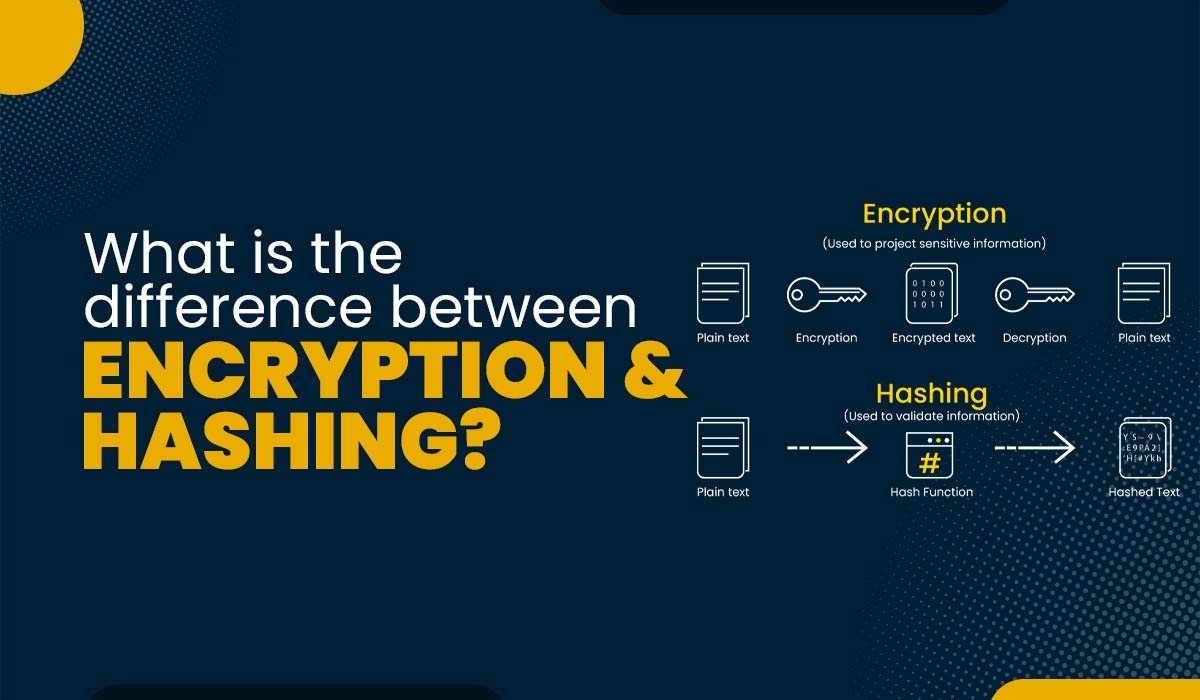
Introduction When it comes to data security, hashing and encryption are the two most crucial foundational operations. Both of these techniques transform the raw data into an entirely different format. The terms Hashing and Encryption are often used in the domain of data security, but do you know what is the difference between encryption and…
-
Can I do DevOps after CCNA?

Introduction “Can I do DevOps after CCNA Training?” is one of network engineers’ most frequently asked questions as the networking industry moves toward advanced technologies. Before getting into further details on whether you can go for DevOps or not after CCNA, let’s understand the basics of CCNA. The CCNA program is designed to validate an…
-
DHCP with IPv6 (DHCPv6) – Everything You Should Know

Introduction The configuration becomes increasingly difficult to understand as the network grows in size and complexity. Additionally, there is a dramatic growth in the number of computers and mobile devices (such as portable laptops or wireless terminals), leading to frequent IP address changes and a lack of available IP resources. Network managers often utilize Dynamic…
-
What is Multicasting in Computer Networks?

Introduction Before starting about multicasting, we have to understand why we need multicast communication and what possible challenges we can face without multicast communication. In this blog, we will cover how multicasting works and how the data is processed in multicast communication, its advantages, multicast forwarding, and everything you need to know about it. Multicast…
-
Network Address Translation || NAT in Networking
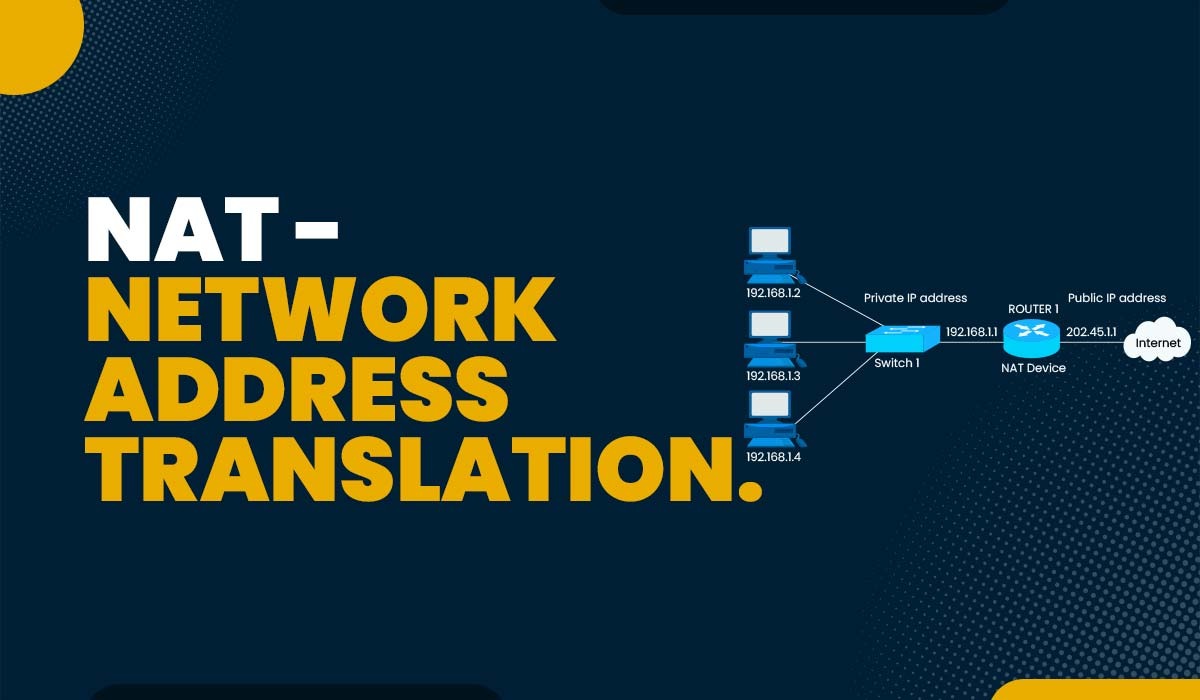
Introduction No one anticipated the rapid growth of the Internet when IP addressing was developed. The shortage of IPv4 addresses directly affects the internet’s rapid expansion. Some addresses (Class D and E) are allocated for multicast, research, and development, reducing the total number of usable IPv4 addresses from the available 2^32, or 4.2 billion. To…
-
EIGRP and OSPF Metric Calculation – Path Calculation Methods
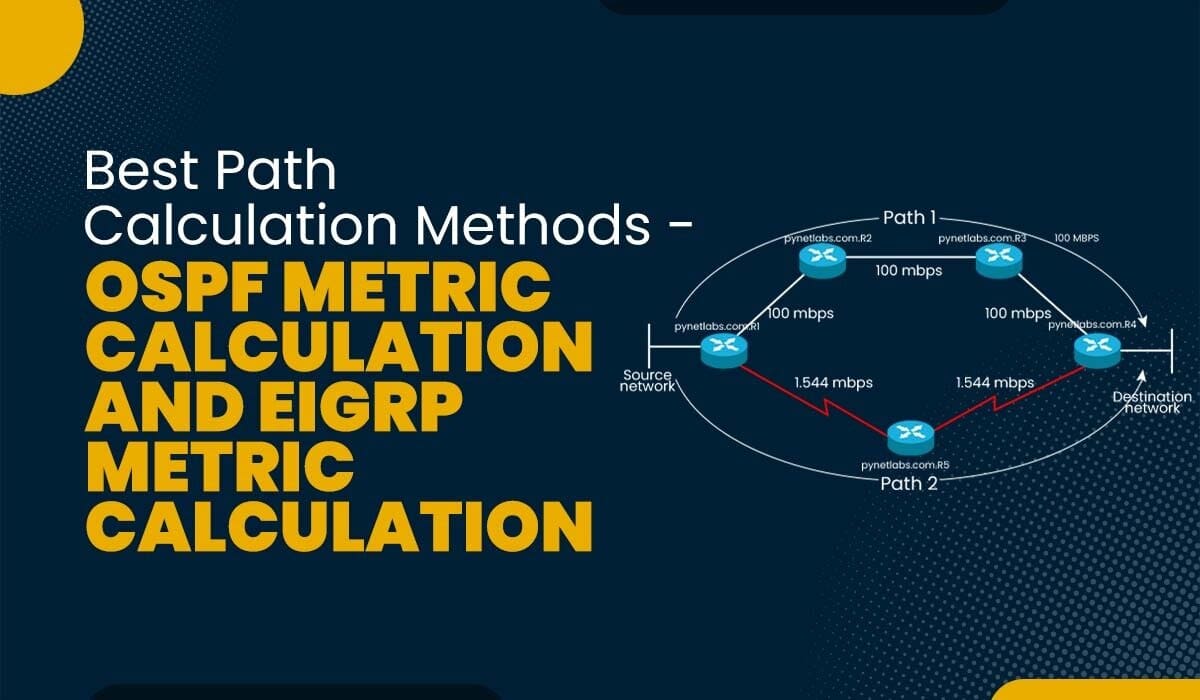
Introduction Metric calculation is a critical component for any routing protocol. OSPF metric calculation is used to find the shortest path by using cost as a metric and determining the cost of paths to know the best path to the destination. Before understanding the OSPF and EIGRP Metric calculation, you need to know that: The…
-
Top 20 OSINT Tools for 2025 (Free and Paid)

Introduction We live in a digital world where everything is online, and that’s where you have to find relevant information about everything. This information can be easily gathered using OSINT tools as the internet world is vast, but it is impossible to find the information you are looking for every time. Does that mean that…
-
AAA in Networking | Authentication, Authorization, and Accounting
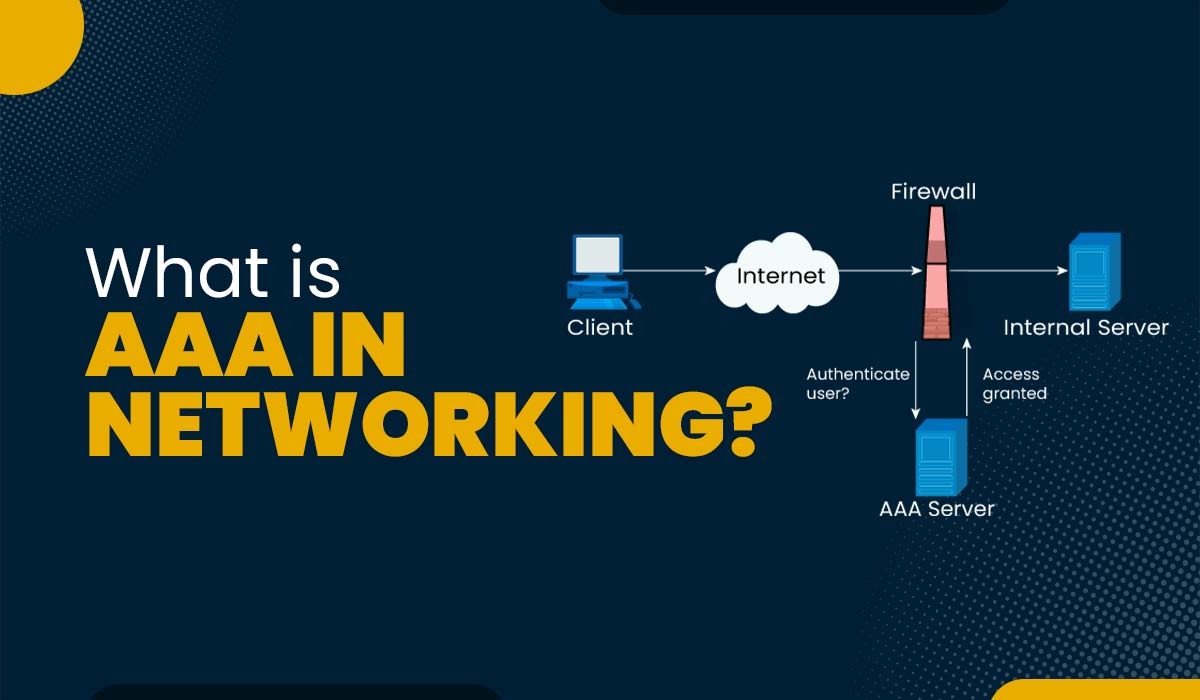
Introduction In the vast realm of networking, AAA is an acronym that frequently appears, yet its meaning and significance often remain elusive to many. If you find yourself grappling with questions like “What is AAA in networking?” or “How does it impact network security?”, then you’ve come to the right place. In this blog, we…
-
What is Access Control List (ACL) in Networking?
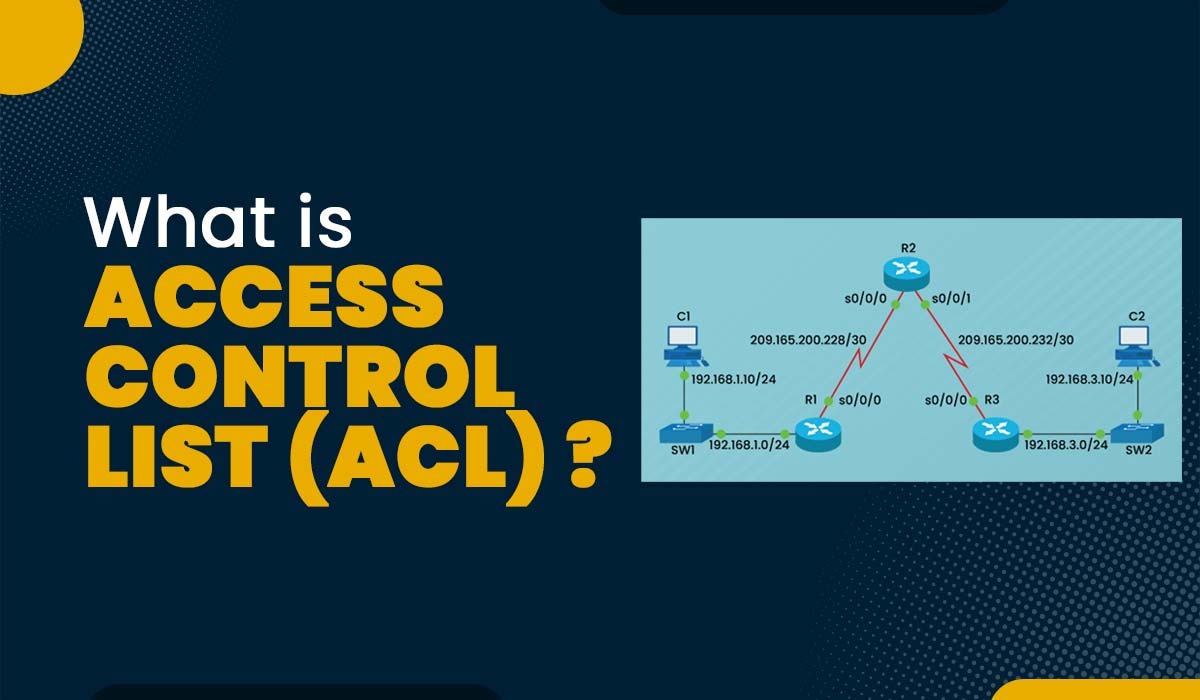
Introduction You may have heard about the Access Control List or ACL. It is used to control permissions to a computer system or network, but do you know what is Access control list? As we know, the Internet is a network of networks, and routers play a vital role in having connectivity between different networks.…
-
What is VLAN (Virtual Local Area Network) and its Types?
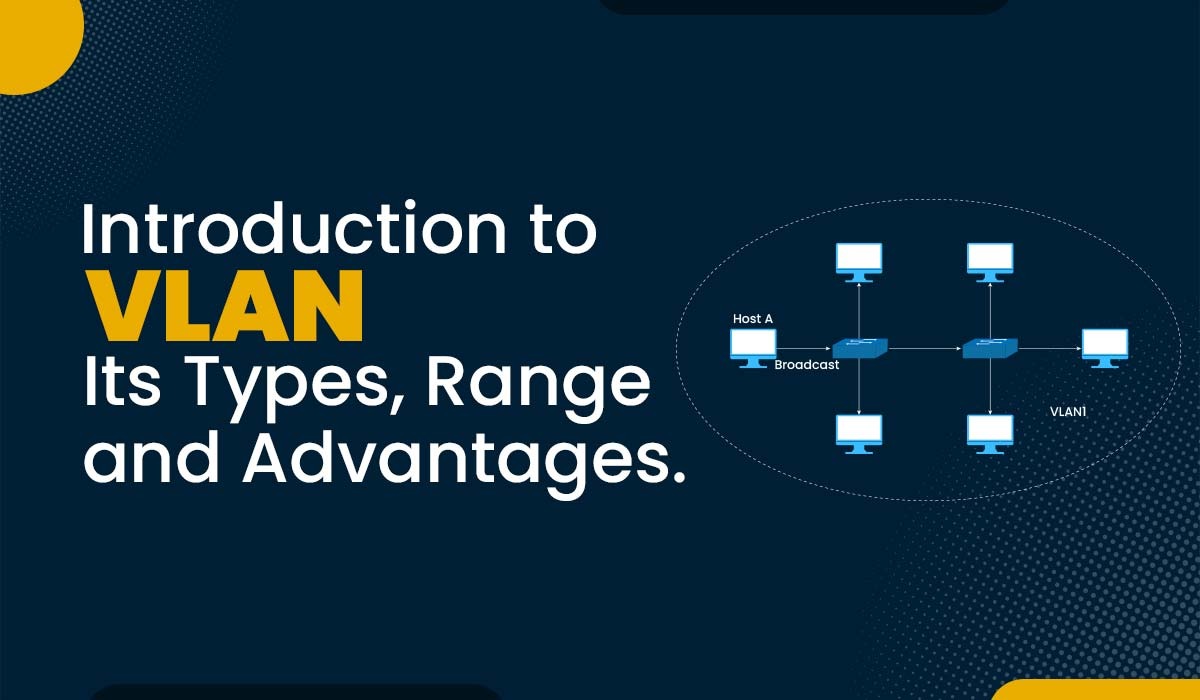
Introduction In networking, as we know, switches are used to create networks, while routers are used to connect different networks. By default, switches forward both broadcast and multicast out of every port but not the originating one. However, if you require to divide a single broadcast domain into smaller ones with security in some networks,…


