-
What is Cisco NSO (Network Services Orchestrator)?

Introduction As time advances, networks become more complex, and traditional manual ways of managing them are no longer good enough. Organizations need to have streamlined network management solutions in order to run networks smoothly. Cisco NSO emerges as a game-changer, offering automation and orchestration capabilities that enable organizations to adapt, scale, and innovate with agility.…
-
SD-WAN vs MPLS – What’s the Difference?
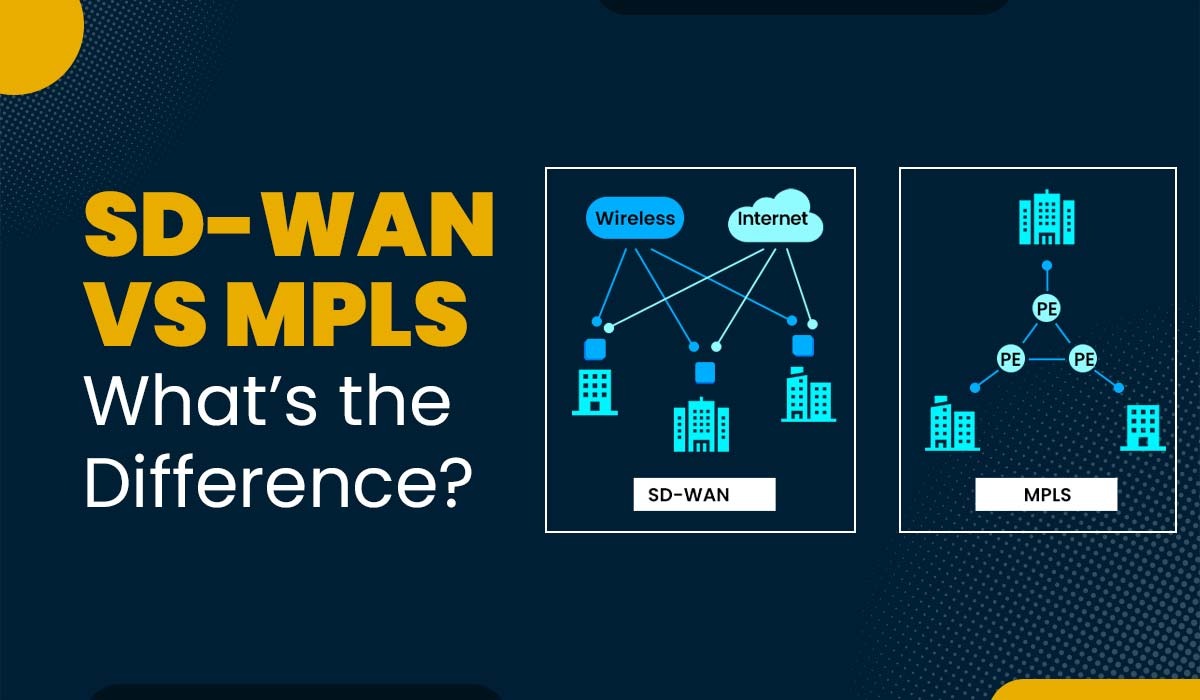
Introduction WAN, or Wide Area Network, plays a major role in connecting computer networks over long distances. It ensures that there should be smooth communication as well as efficient data transfer between different locations. Companies and network engineers rely heavily on WAN technologies to link their offices, data centers, and remote sites. There are two…
-
What are the Different Types of WANs?

Introduction In today’s world of connectivity, Wide Area Networks (WANs) play a major role in connecting different networks irrespective of the location. This further assists in smooth communication and data transfer among clients and organizations. As cloud computing and remote work become more prevalent, having a good knowledge of the WAN types is crucial for…
-
What is VAPT (Vulnerability Assessment and Penetration Testing)?
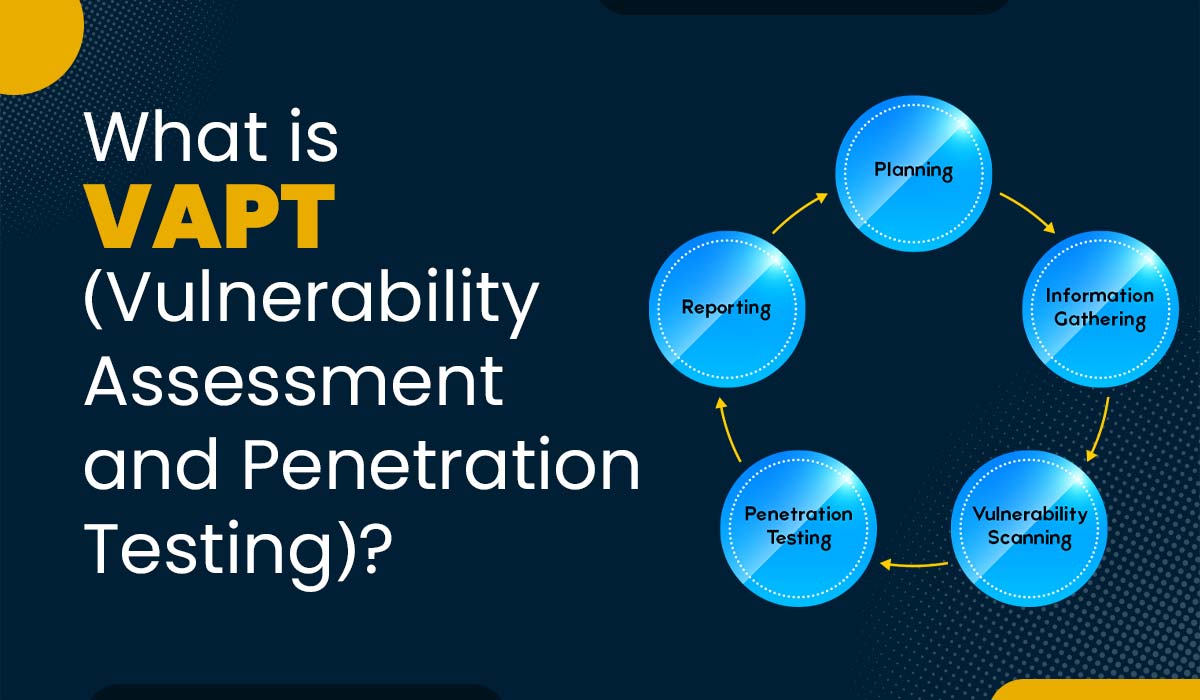
Introduction Nowadays, cybercrimes have seen a massive increase due to the development of new technologies and our reliance on Internet usage. Hackers and cybercriminals are trying to find newer ways to exploit vulnerabilities in systems and networks to steal sensitive information. This, in return, poses a serious threat to businesses, organizations, and individuals. Vulnerability assessment…
-
Top 20 OSI Model Interview Questions and Answers (2025)
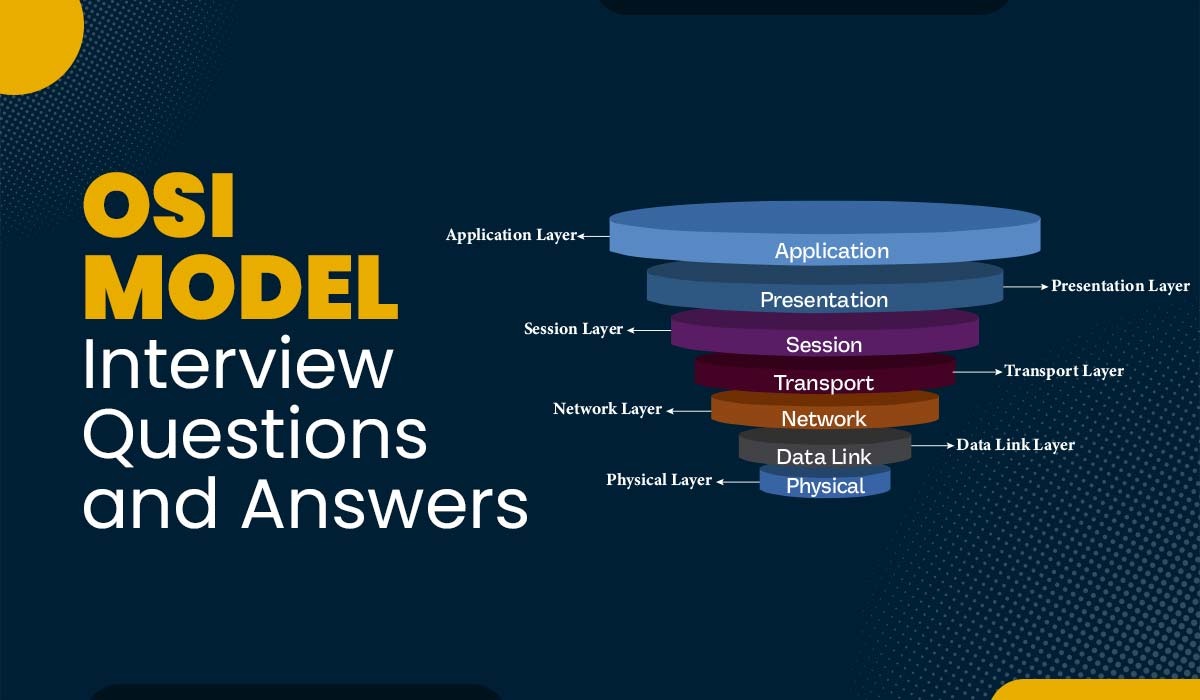
Introduction If someone is preparing for a network-related job interview, it is possible that they may encounter some questions based on the OSI model. In order to help students clear their interviews, we have hand-picked some of the most asked and important OSI model Interview questions and answers for freshers as well as working professionals.…
-
How Does Packet Flow in Network?
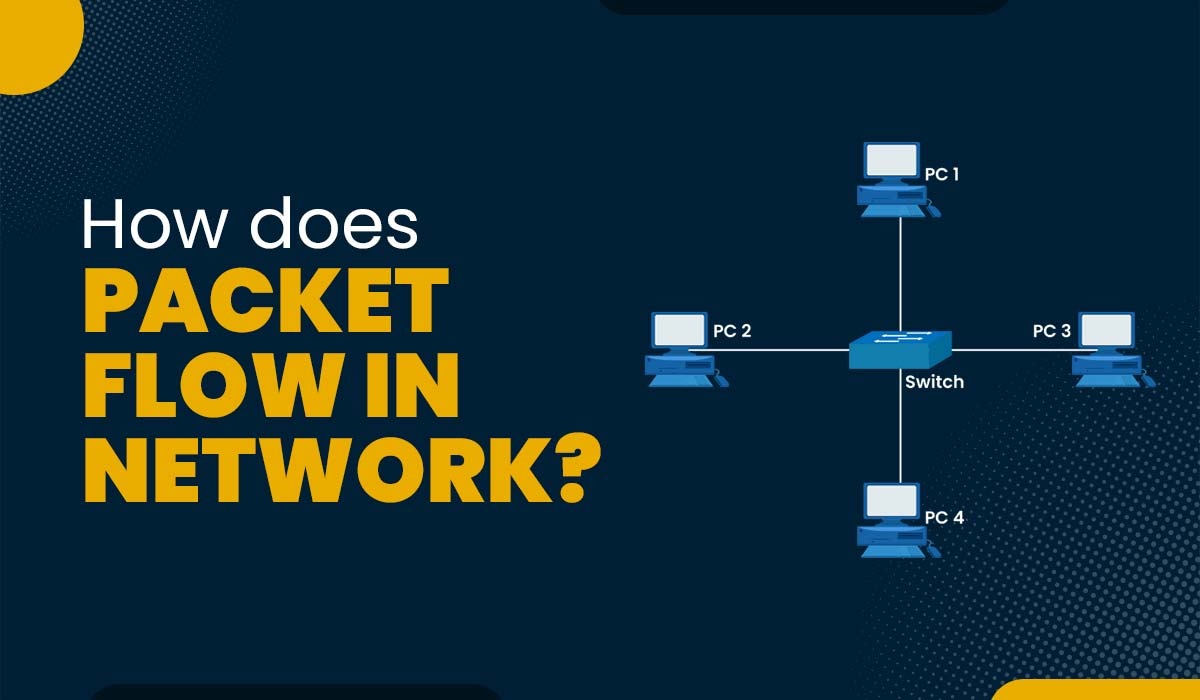
Introduction Packets are the basic units of data that are transmitted over a network. A packet is a small piece of information that contains the source and destination addresses, the data itself, and some additional information for error checking and routing. Packets are sent from one device to another through various intermediate devices, such as…
-
What is PIM Protocol (Protocol Independent Multicast)?
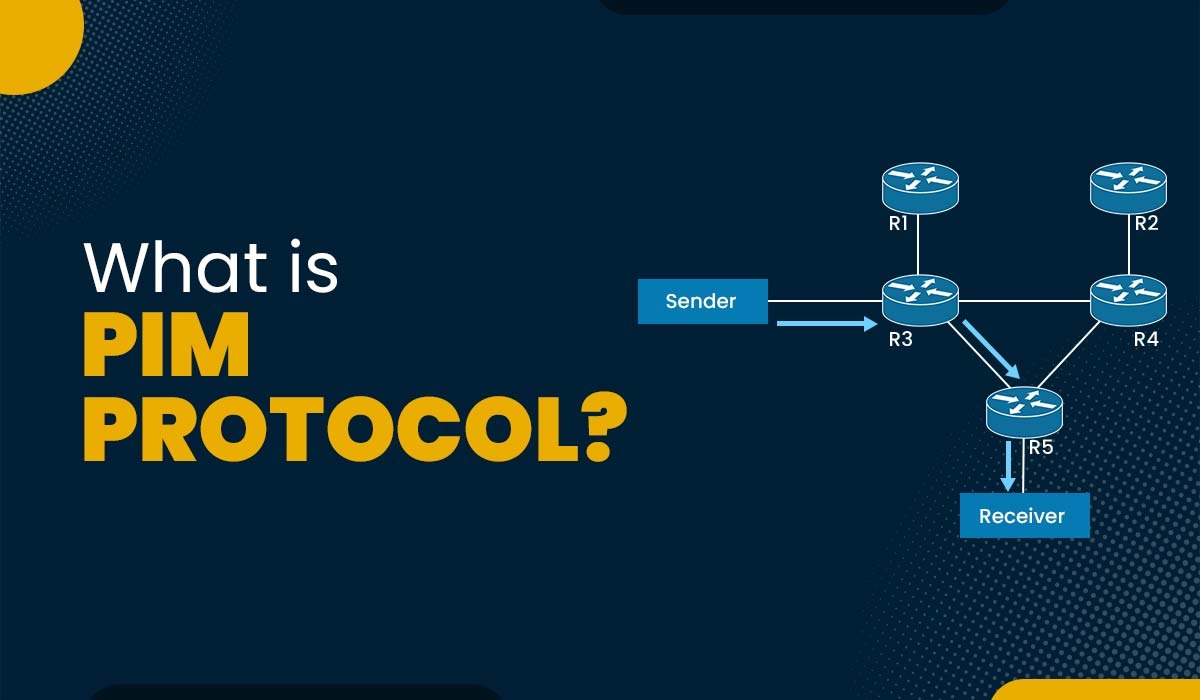
Introduction Multicast is a technique that allows one source to send data to multiple destinations simultaneously without duplicating the data packets. This can save bandwidth and improve network efficiency, especially for applications that involve streaming media, online gaming, video conferencing, or distributed computing. However, multicast routing is a challenging task, as it requires the network…
-
What is Network Function Virtualization (NFV)?
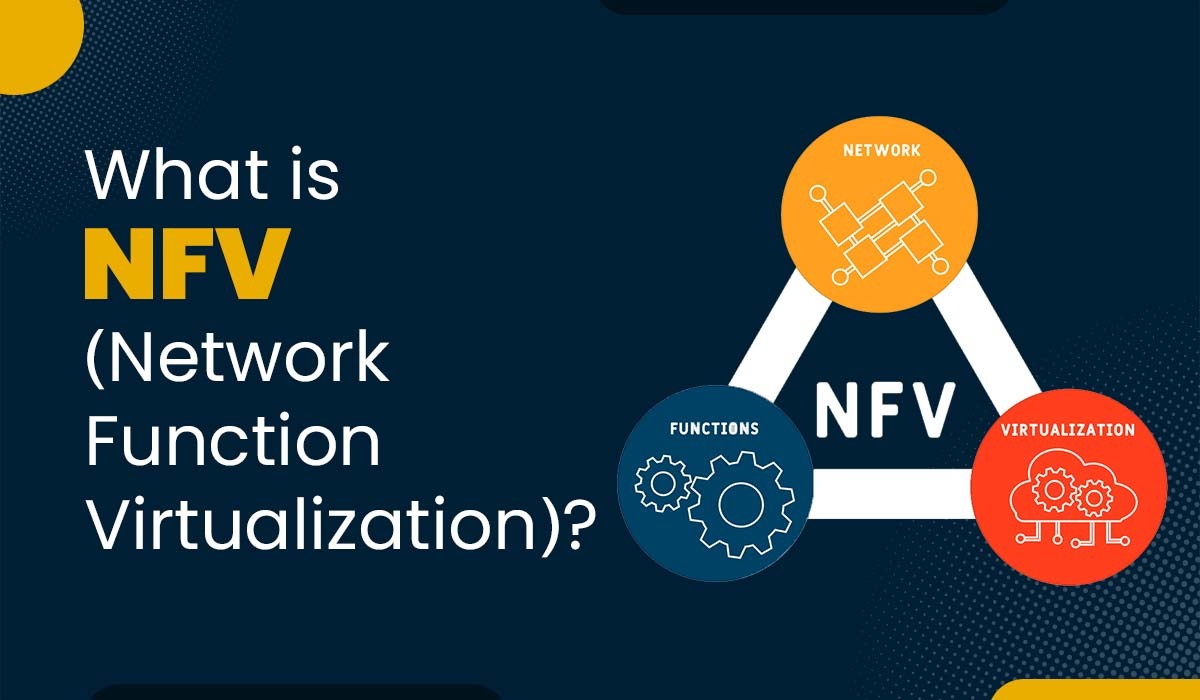
Introduction NFV stands for Network Function Virtualization, and it’s a way of running network services, such as routers, firewalls, and load balancers, on virtual machines (VMs) instead of physical hardware. This means one doesn’t need to buy expensive and specialized hardware for each network function. One can just use standard servers and run multiple functions…
-
What is Cisco ASA (Adaptive Security Appliances)?
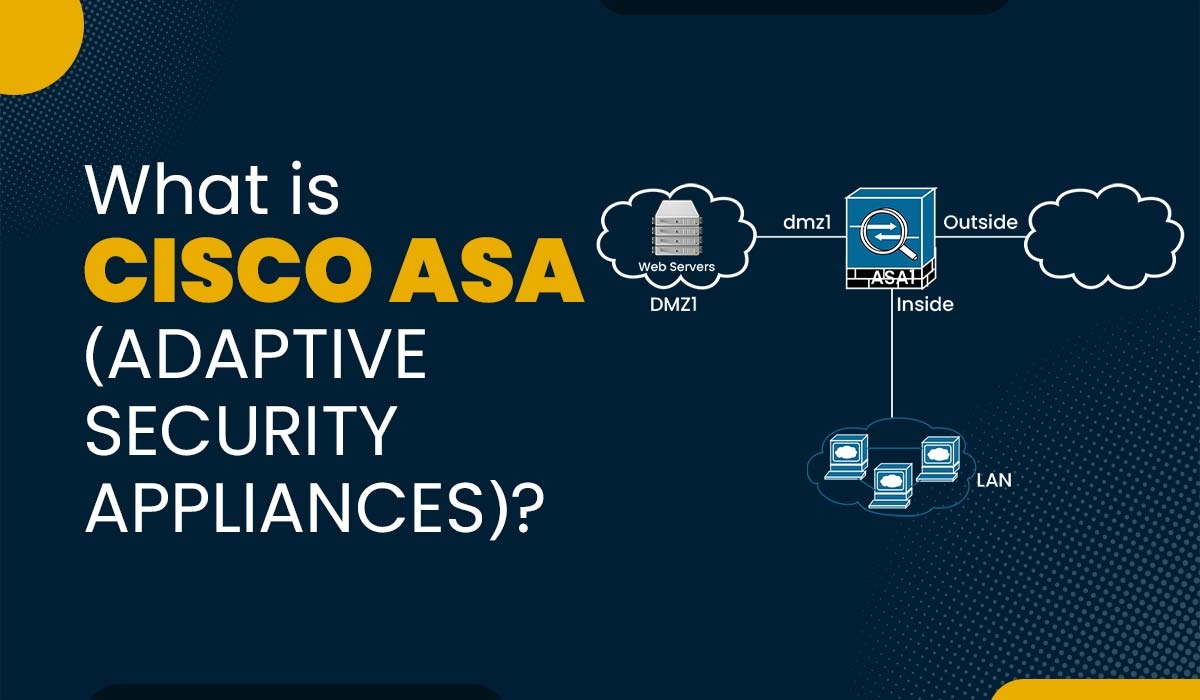
Introduction Nowadays, network security is more than crucial for any organization that completely relies on the Internet for its operations. Cyberattacks can lead to an impact on the integrity, confidentiality, and availability of data as well as network resources. Therefore, it is mandatory for all to have a robust network security solution that can protect…
-
What is Device Hardening and its Different Types?
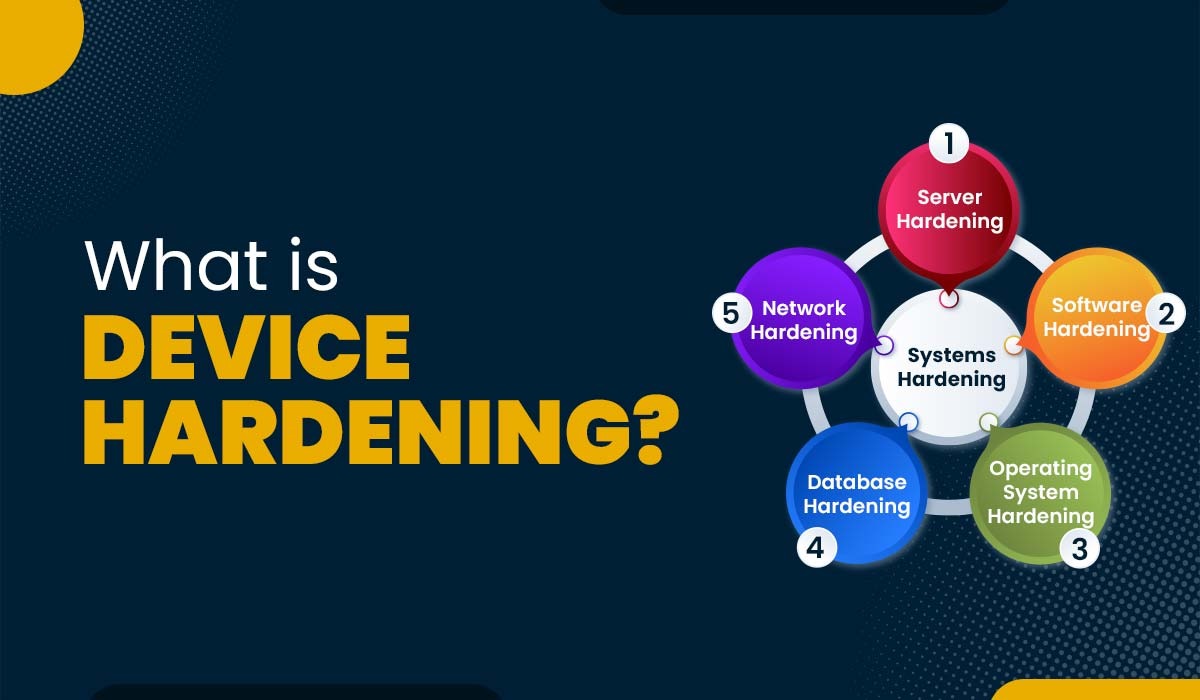
Introduction The internet has completely transformed how we communicate, work, learn, and entertain ourselves. It has also brought new opportunities for innovation, collaboration, and creativity. Along with these opportunities come risks. Cyberthreats are constantly becoming more sophisticated, targeting not only large organizations and governments but also individuals and small businesses. These cyberattacks can compromise the…


