-
What is GRE (Generic Routing Encapsulation) Protocol?

Introduction Generic Routing Encapsulation, or GRE, is a tunneling system that allows various network layer protocols to be encapsulated within IP tunnels. Using either public or private networks, GRE may establish point-to-point logical links between network devices. In this blog, we will explain the GRE protocol with its working, benefits, drawbacks, and configuration. What is…
-
Control Plane vs Data Plane – What’s the Difference?

Introduction The control plane and data plane are integral parts of a network. Each plane performs specific functions and responsibilities to ensure efficient packet flow within the network. Understanding the basic difference between the two is crucial for effectively designing and optimizing networks that further assist in enhancing performance as well as security. In this…
-
Best Networking Courses for Beginners in 2025

Introduction In today’s digital world, its a must for anyone to learn a skill that aligns not only with their career but also with the company’s needs. Networking is a skill that is in high demand, and it can open up many career opportunities for you in different sectors such as IT, Telecom, government, education,…
-
Various OSPF States Explained – A Detailed Guide
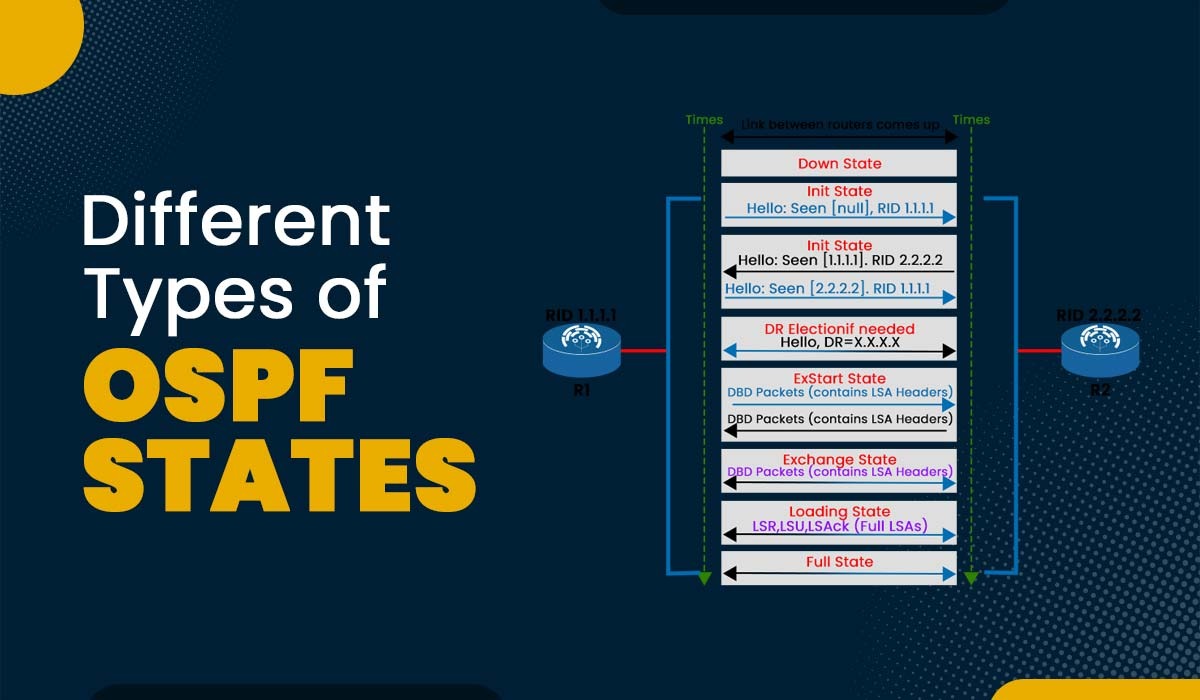
Introduction To achieve complete adjacency, OSPF routers undergo many states. In this blog, we will discuss the progression of OSPF states, from Down State to the Full State. Additionally, we will look at the requirements that must be met for OSPF to transition from one state to the next. It is important to note that…
-
Difference between Subnetting and Supernetting
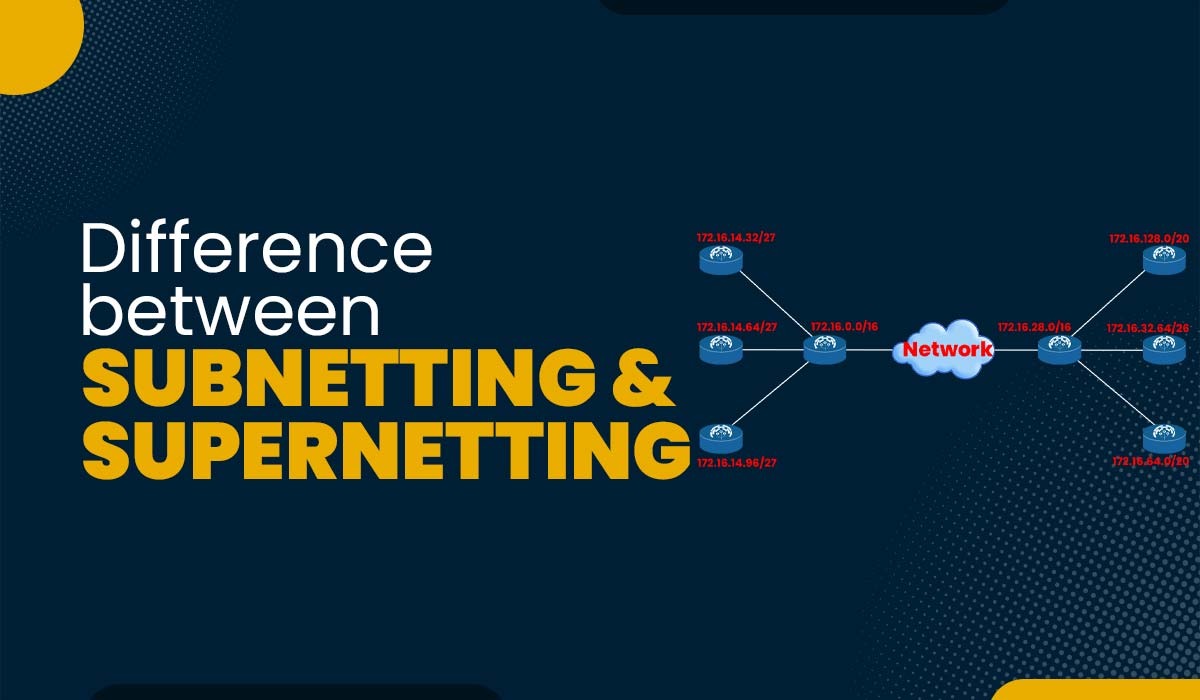
Introduction A network is a collection of two or more computers that can communicate with one another to share data and resources. A device within a network is identified uniquely through the use of IP addresses. Subnetting and Supernetting are two methods used to organize IP addresses. Subnetting is a method of breaking a huge…
-
What are the 8 Different Types of Firewalls?

Introduction Finding the right tools may be difficult for businesses thinking about protecting sensitive information. When it comes to keeping sensitive data safe, every system may benefit from using any number of easily accessible tools. Installing a firewall can prevent unauthorized access to your network and its components. In this Blog, we will focus on…
-
What is Collision Domain in Networking?

Introduction In the networking field, various network devices are utilized for different purposes. Hubs, switches, routers, and other network devices are utilized to perform different tasks within a network infrastructure. In order to analyze the functionality and effectiveness of network devices, various metrics, defined as standards or systems of measurement, are used. The Collision domain…
-
CSMA CD vs CSMA CA – What’s the difference?
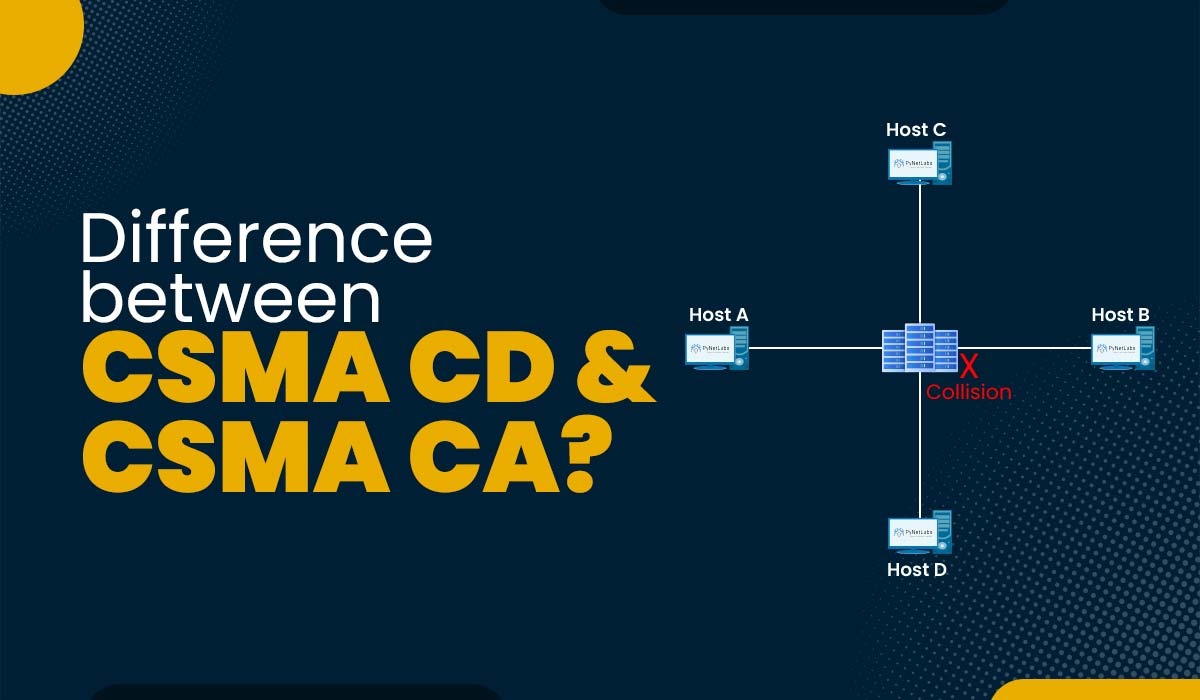
Introduction The ability of multiple network computers to transmit data to each other without experiencing significant packet collisions is truly remarkable. One could expect various issues due to the vast number of data packets transmitted across a typical network. However, it is important to note that the majority of modern computer networks display a high…
-
What is IPSec (Internet Protocol Security)?

Introduction Nowadays, most organizations rely heavily on the Internet for daily business; as a result, there has been a surge in cyberattacks. As cybercrime becomes more common, businesses find it difficult to protect sensitive data without compromising productivity. That’s why IPSec is widely used by businesses to allow secure transmission and access of data. But…
-
VRRP in Networking || Virtual Router Redundancy Protocol

Introduction VRRP in Networking stands for Virtual Router Redundancy Protocol, and it is a protocol that provides high availability and fault tolerance for routers in a network. It allows multiple routers to form a virtual router group and share a virtual IP address, which is used as the default gateway for the hosts in the…


