-
Various kinds of OSI Layer Attacks || All 7 Layers
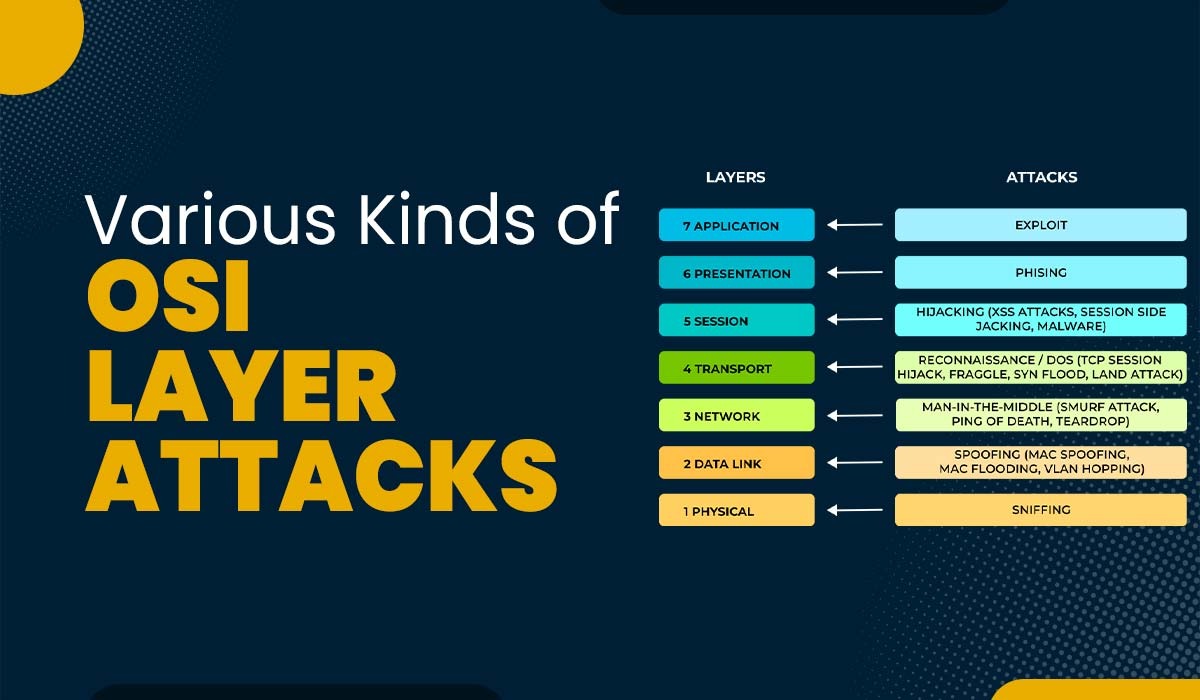
Introduction Cybersecurity is a dynamic field since hackers are always developing new methods of breaking into networks and stealing private data. Understanding the many forms of OSI layer attacks and strategies of cyberattacks is vital for establishing a successful defense against them. It is essential to understand the different kinds of cyberattacks at each layer…
-
What are the 5 Phases of Ethical Hacking?

Introduction With the increasing number of organizations shifting to the digital world, the importance of protecting data from hacking and cyber-attacks has become more critical than ever. Many companies are now recognizing the potential risks associated with these attacks and considering proactive measures, such as ethical hacking. But how can ethical hacking help in saving…
-
Difference between Active Attack and Passive Attack (2025)
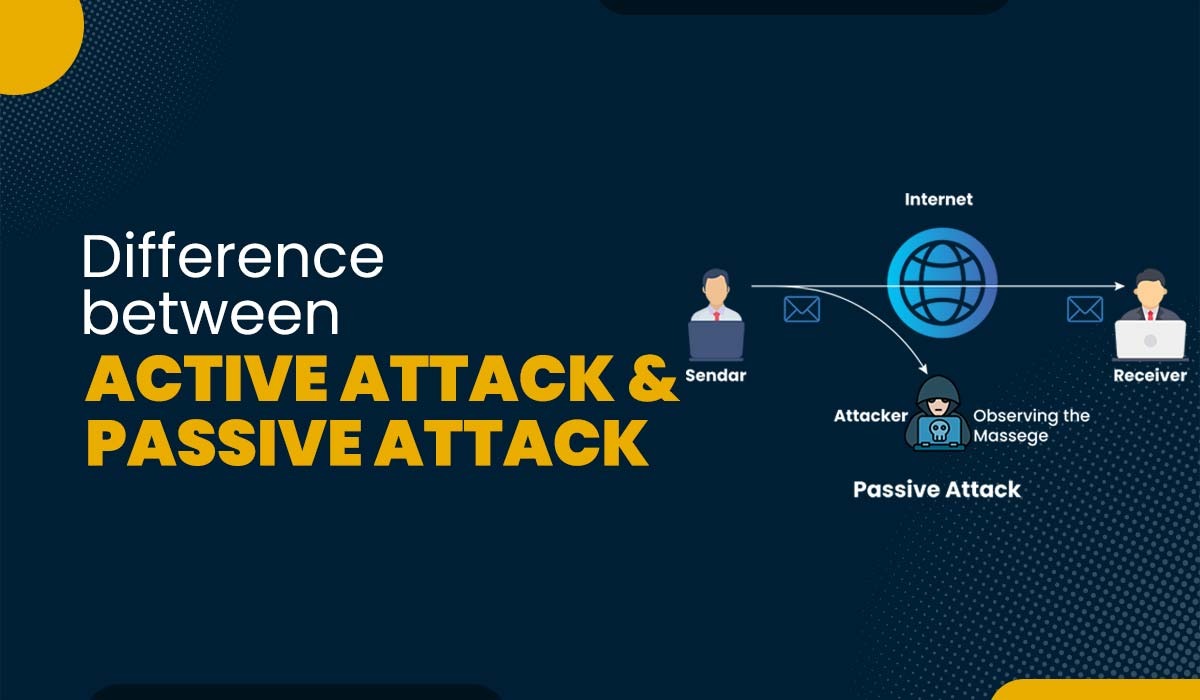
Introduction Clearly, the Internet is one of the most significant innovations of our time. It has simplified our life in more ways than we can even count. This development has similarly exposed us to a wide variety of cyberattacks. Cybersecurity attacks pose a greater threat to all that is part of the Internet. Cybersecurity threats…
-
What is Bluetooth Hacking and How to Prevent It?
Introduction There is less need for wired connections as new innovations in smartphones and other devices become more widespread. These days, Bluetooth wireless communication is used by the vast majority of devices to establish wireless connections. Wireless devices are becoming increasingly popular because they allow users to stay connected without carrying cumbersome cables and wires.…
-
Top 20 Penetration Testing Interview Questions and Answers

Introduction In today’s world, cyberattacks pose several threats to many companies. Therefore, it is of the utmost importance that trained specialists capable of conducting penetration tests have the knowledge to take the measures required to discover all the security gaps and risks hiding in an IT network or an organization. Now, if you want to…
-
Top 20 Ethical Hacking Interview Questions and Answers

Introduction Whether a government agency or a private company, almost all operations nowadays have some internet presence, making them vulnerable to security breaches, data loss, financial losses, and other damages. Corporations use ethical hacking to detect potential threats like malware, viruses, and ransomware on a computer or network to prevent further damage and improve security.…
-
Top Cyber Security Interview Questions and Answers (2025)

Introduction While attending a job interview, one should have the confidence and the clarity to crack it effortlessly. This handpicked collection of the top cyber security interview questions and answers for a cyber-security job interview aims to help you prepare effectively for your next cyber security job interview. However, depending on the scope of the…
-
Top 20 OSINT Tools for 2025 (Free and Paid)

Introduction We live in a digital world where everything is online, and that’s where you have to find relevant information about everything. This information can be easily gathered using OSINT tools as the internet world is vast, but it is impossible to find the information you are looking for every time. Does that mean that…


