-
What is the purpose of an SSL Certificate in Cyber Security?
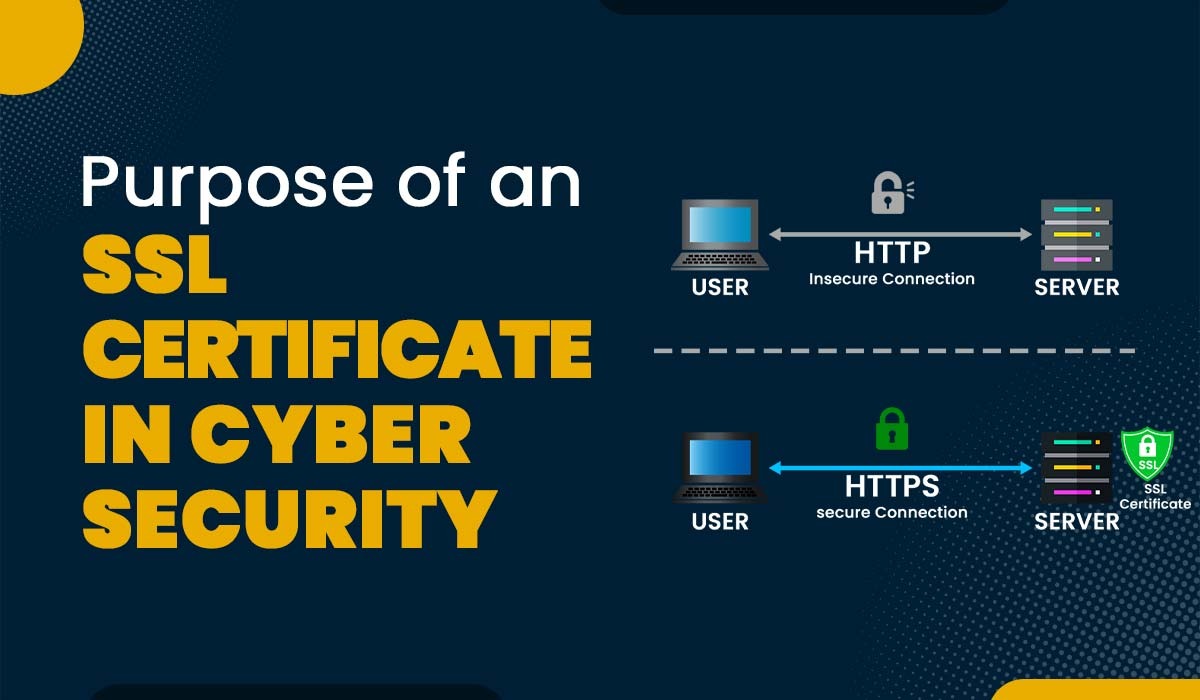
Introduction This article explores an important aspect of cyber security; the SSL certificate. It explains how the certificate works, what its benefits are, and why it is so crucial in cyber security. We begin with the basic question: What is an SSL certificate in Cyber Security? An SSL certificate is a digital certificate issued by…
-
Top 5 Cyber Security Course with Job Guarantee (2025)

Introduction As the world becomes more interconnected, Cybersecurity has become more crucial than ever for all individuals, businesses, and government entities. There is a massive demand for skilled cybersecurity professionals in order to protect against cyber threats. If someone is thinking of making a career in the field of Cybersecurity, it is the right time…
-
Top 10 IT Courses with Job Guarantee (2025)

Introduction With the rapid advancement in technology, individuals must go for IT courses that will help them acquire specialized skills that are in high demand. For beginners especially, it can be challenging to get a job in the present competitive market. Now, how do students get job assurance after completing IT courses? This is where…
-
What is VAPT (Vulnerability Assessment and Penetration Testing)?
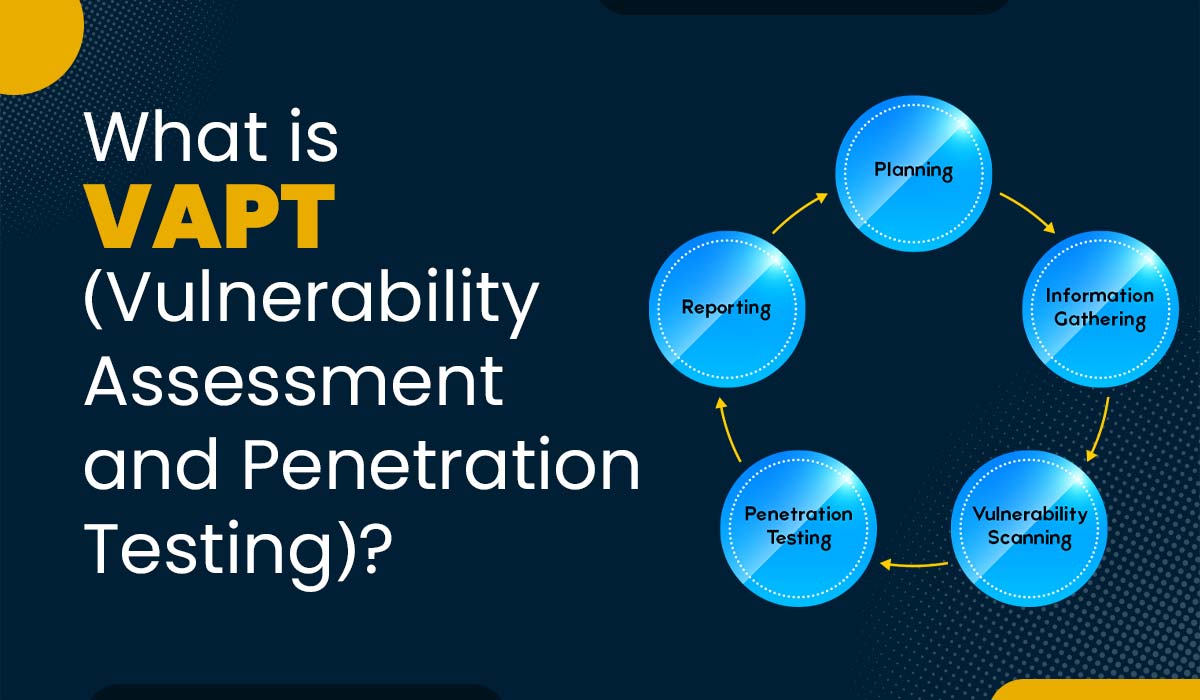
Introduction Nowadays, cybercrimes have seen a massive increase due to the development of new technologies and our reliance on Internet usage. Hackers and cybercriminals are trying to find newer ways to exploit vulnerabilities in systems and networks to steal sensitive information. This, in return, poses a serious threat to businesses, organizations, and individuals. Vulnerability assessment…
-
What is Device Hardening and its Different Types?
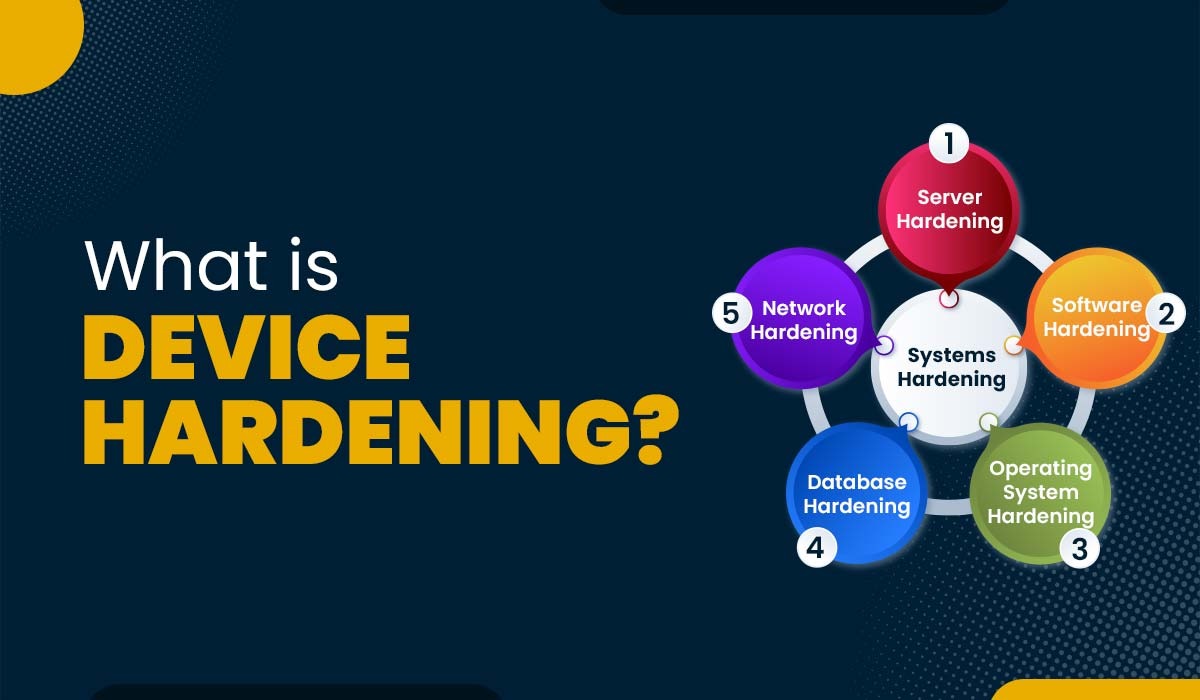
Introduction The internet has completely transformed how we communicate, work, learn, and entertain ourselves. It has also brought new opportunities for innovation, collaboration, and creativity. Along with these opportunities come risks. Cyberthreats are constantly becoming more sophisticated, targeting not only large organizations and governments but also individuals and small businesses. These cyberattacks can compromise the…
-
Objectives of Cyber Security

Introduction As technology advances, so does the reliance of businesses on digital services and networks. We all are either directly or indirectly dependent on the security and integrity of online systems in order to protect personal data as well as business operations. Cybersecurity is of utmost importance nowadays, as we all know that cyberattacks can…
-
Is Cyber Security a Good Career?

Introduction Cybersecurity is the method of protecting networks, systems, devices, and information from cyberattacks. It is crucial in the digital world, as cyber threats are continuously evolving, and as a result, it can affect the integrity of data. Cyber security is not only critical for individuals and agencies but also for the nation as a…
-
How to Start a Cybersecurity Career in India?

Introduction A cybersecurity career stands out as one of the best and is in demand worldwide. As our digital landscape grows increasingly, data, systems, and networks are needed to be protected from cyber threats. The realm of Cybersecurity can bring about changes in one’s life in many ways. It presents a challenging and captivating career…
-
Difference between Symmetric and Asymmetric Key Cryptography

Introduction Scammers and other cyber criminals are getting more active in today’s society, harming millions of consumers. It is essential to encrypt everything to stop these people from stealing priceless data. Fortunately, three alternative encryption techniques may be used: symmetric encryption, asymmetric encryption, and hash functions (Keyless). In this blog, we will be mainly focusing…
-
What is VPN in Cyber Security and its Types?

Introduction Nowadays, everyone relies heavily on digital platforms, whether for business purposes or some important transactions. With the increase in digital presence, protecting personal data from hackers is crucial. VPN in cyber security is one approach to stop third parties from obtaining vital data for their benefit. In this blog, we will discuss what a…


