-
What is IGMP Snooping?
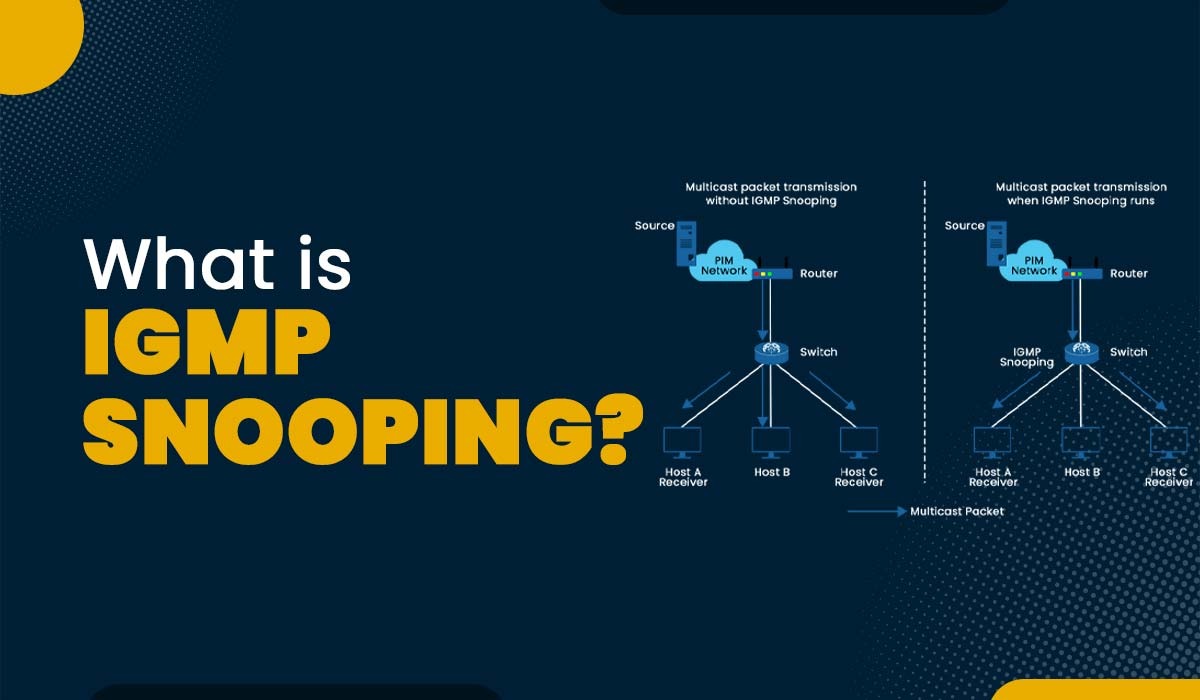
Introduction Today’s data transmission demands can’t be met by the inefficient and resource-intensive unicast method used by most networks. Internet Group Management Protocol (IGMP) Snooping was developed as a solution and is now often implemented in network multicast mode. In this blog, we will explain IGMP snooping, its working, functions, and applications. Let’s begin with…
-
Various kinds of OSI Layer Attacks || All 7 Layers
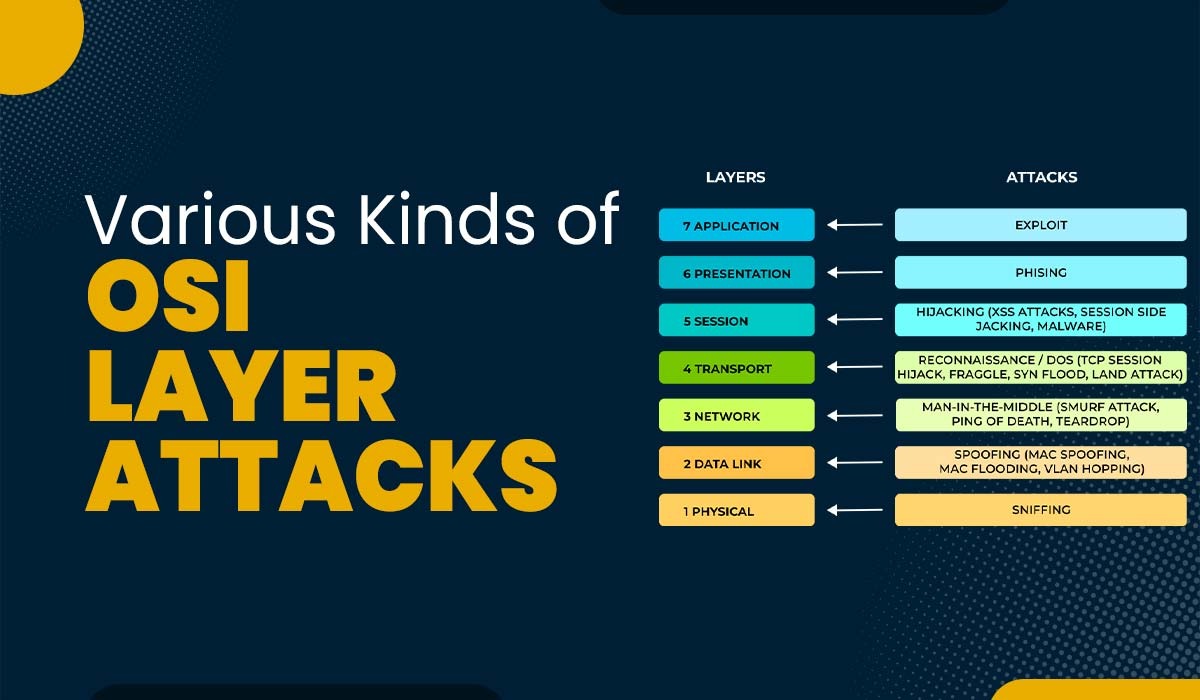
Introduction Cybersecurity is a dynamic field since hackers are always developing new methods of breaking into networks and stealing private data. Understanding the many forms of OSI layer attacks and strategies of cyberattacks is vital for establishing a successful defense against them. It is essential to understand the different kinds of cyberattacks at each layer…
-
What is a Subnet and How Subnetting Works?
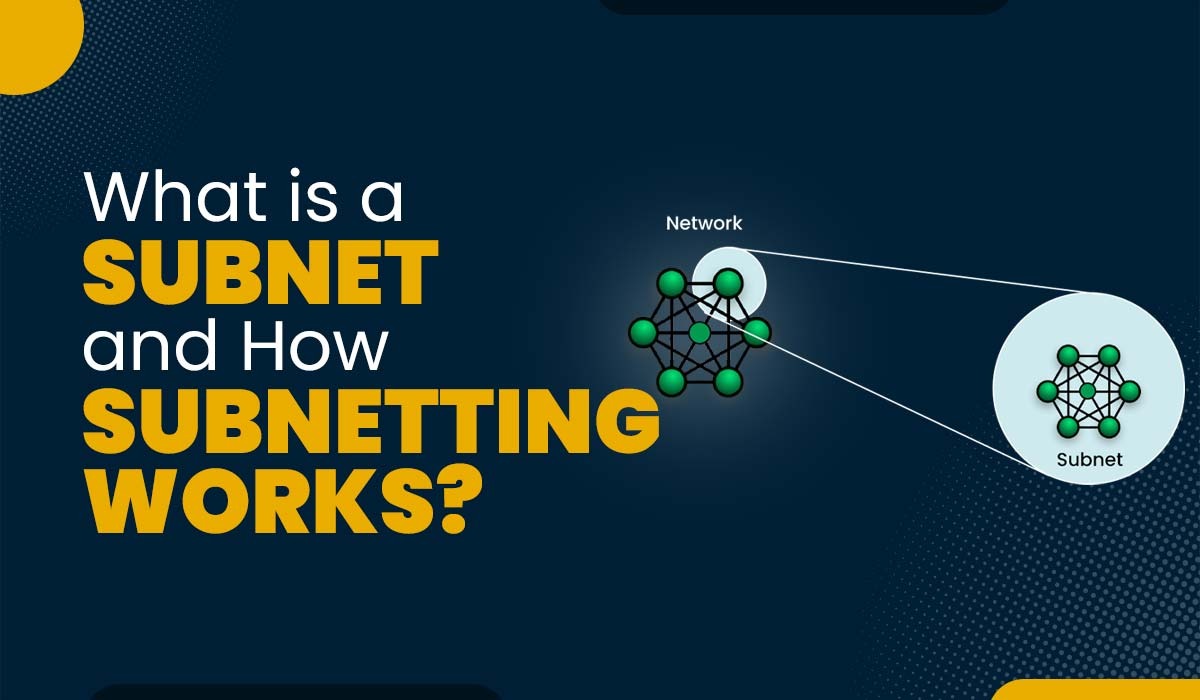
Introduction The management of a network on a major scale is not easy. As networks continue to grow in size and complexity, network engineers are faced with the challenge of determining optimal routes for handling the substantial volume of traffic flowing through them. Subnetting is one of the solutions developed, but the question is, what…
-
What is GRE (Generic Routing Encapsulation) Protocol?

Introduction Generic Routing Encapsulation, or GRE, is a tunneling system that allows various network layer protocols to be encapsulated within IP tunnels. Using either public or private networks, GRE may establish point-to-point logical links between network devices. In this blog, we will explain the GRE protocol with its working, benefits, drawbacks, and configuration. What is…
-
Control Plane vs Data Plane – What’s the Difference?

Introduction The control plane and data plane are integral parts of a network. Each plane performs specific functions and responsibilities to ensure efficient packet flow within the network. Understanding the basic difference between the two is crucial for effectively designing and optimizing networks that further assist in enhancing performance as well as security. In this…
-
Best Networking Courses for Beginners in 2025

Introduction In today’s digital world, its a must for anyone to learn a skill that aligns not only with their career but also with the company’s needs. Networking is a skill that is in high demand, and it can open up many career opportunities for you in different sectors such as IT, Telecom, government, education,…
-
Various OSPF States Explained – A Detailed Guide
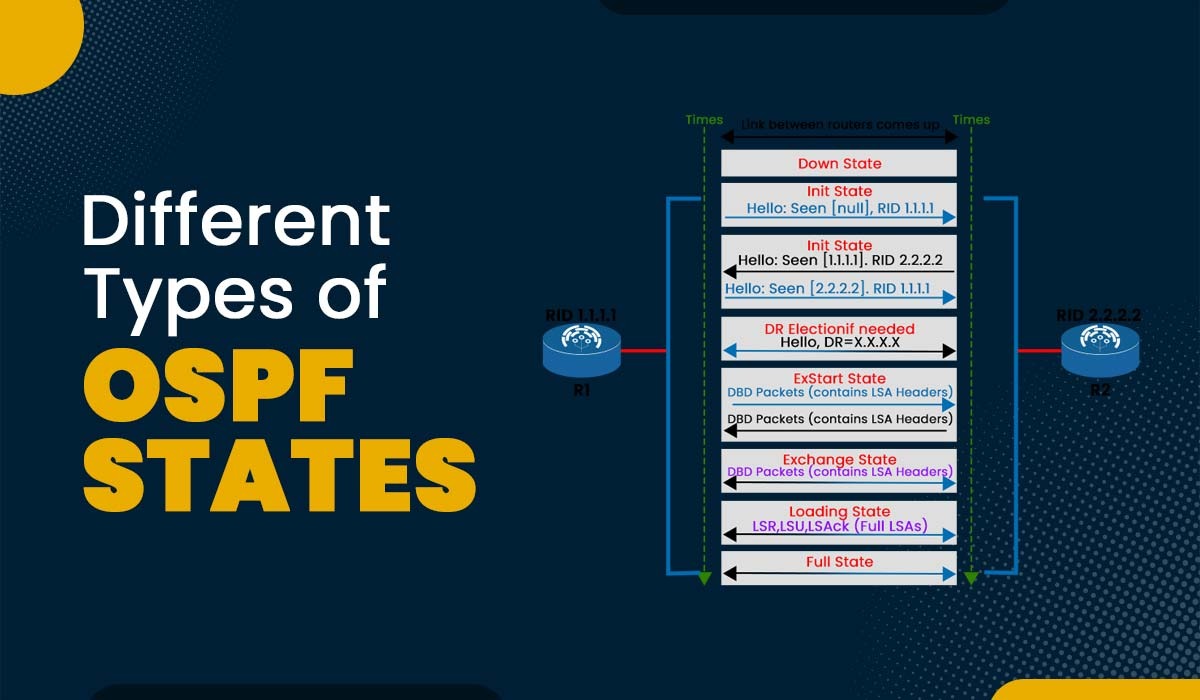
Introduction To achieve complete adjacency, OSPF routers undergo many states. In this blog, we will discuss the progression of OSPF states, from Down State to the Full State. Additionally, we will look at the requirements that must be met for OSPF to transition from one state to the next. It is important to note that…
-
Difference between Subnetting and Supernetting
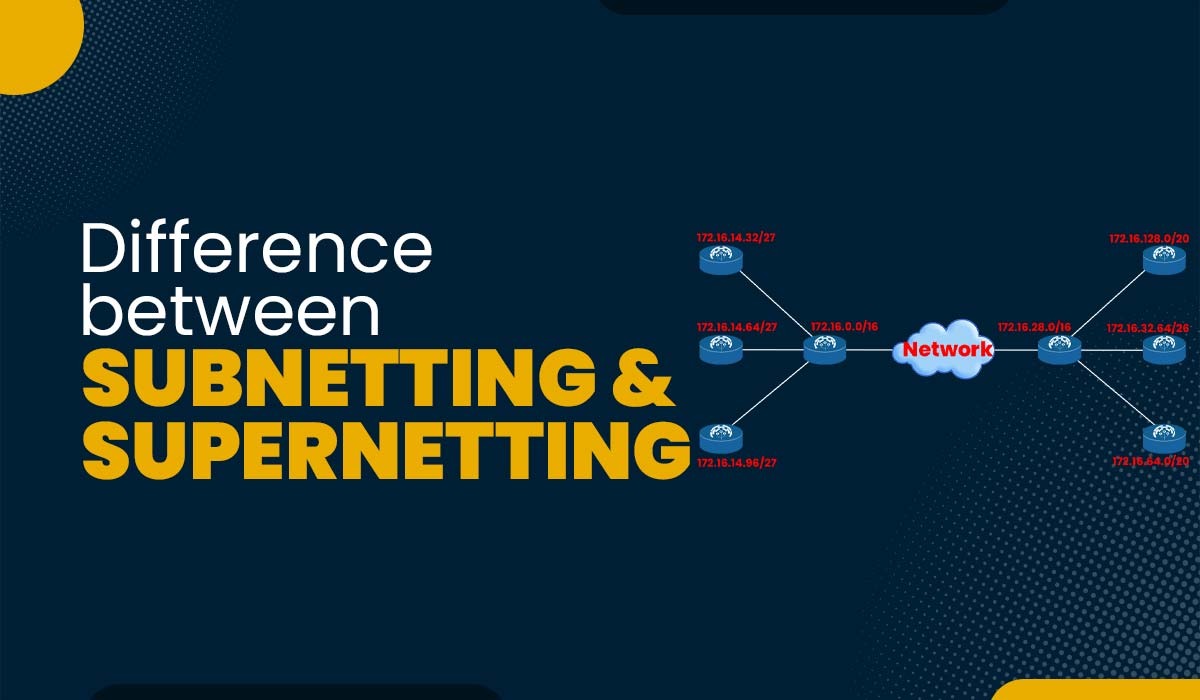
Introduction A network is a collection of two or more computers that can communicate with one another to share data and resources. A device within a network is identified uniquely through the use of IP addresses. Subnetting and Supernetting are two methods used to organize IP addresses. Subnetting is a method of breaking a huge…
-
What are the 8 Different Types of Firewalls?

Introduction Finding the right tools may be difficult for businesses thinking about protecting sensitive information. When it comes to keeping sensitive data safe, every system may benefit from using any number of easily accessible tools. Installing a firewall can prevent unauthorized access to your network and its components. In this Blog, we will focus on…
-
What are the 5 Phases of Ethical Hacking?

Introduction With the increasing number of organizations shifting to the digital world, the importance of protecting data from hacking and cyber-attacks has become more critical than ever. Many companies are now recognizing the potential risks associated with these attacks and considering proactive measures, such as ethical hacking. But how can ethical hacking help in saving…