-
What is Wildcard Mask in Networking?

Introduction Anyone who has worked with networking devices, such as routers and switches, may have heard of the term wildcard mask. A wildcard mask is a way of specifying a range of IP addresses for different purposes, some of which are access control lists, rioting protocols such as OSPF, and network address translation. But the…
-
Top 10 Most Popular Network Simulation Tools (2025)

Introduction Network Simulation is a technique by which one can easily create a virtual representation of the network. This virtual representation can either be used for testing, learning, or research purposes. With the help of network simulation tools, users can design, configure, and analyze different network scenarios without relying on hardware or software. Apart from…
-
Objectives of Network Security

Introduction Nowadays, almost every business has shifted online to offer their services. Companies now have more valuable information than ever before, and securing that information is critical to their success. Effective network security functions as a gatekeeper, prohibiting unwanted access, abuse, modification, or manipulation of a computer network and its resources. In this blog, we…
-
TCP Header – Definition, Diagram and its Format
Introduction TCP, or Transmission control protocol, is a widely used protocol on the Internet that is reliable and connection oriented. TCP operates at the transport layer of the OSI model and ensures the correct ordered delivery of data packets from sender to receiver in a network. TCP is used by many applications that are totally…
-
What is MPLS (Multiprotocol Label Switching)?
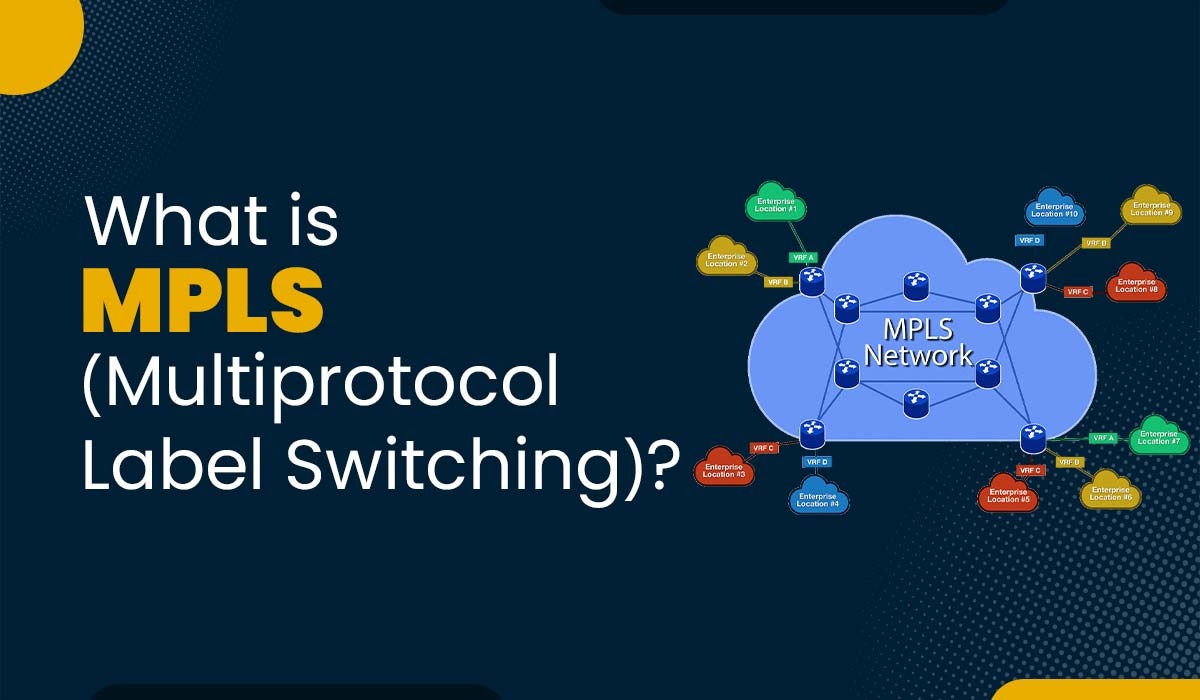
Introduction Multiprotocol Label Switching is a technology that allows efficient data transmission across networks. Network operators and service providers widely employ it to ensure high quality as well as reliable services for their customers. By understanding the working principles of MPLS, one can proficiently design, configure, troubleshoot, and optimize these networks. In this blog post,…
-
IPv4 Header Format, Diagram, and its Significance
Introduction Internet Protocol version 4, or IPv4, is one of the most widely used protocols for sending or receiving data over different kinds of networks. It is a connectionless protocol and does not guarantee the delivery of data, order, or integrity of the packets. Furthermore, it is used to provide a logical connection between the…
-
What is a Virtual Network? How it Works and Its Types?
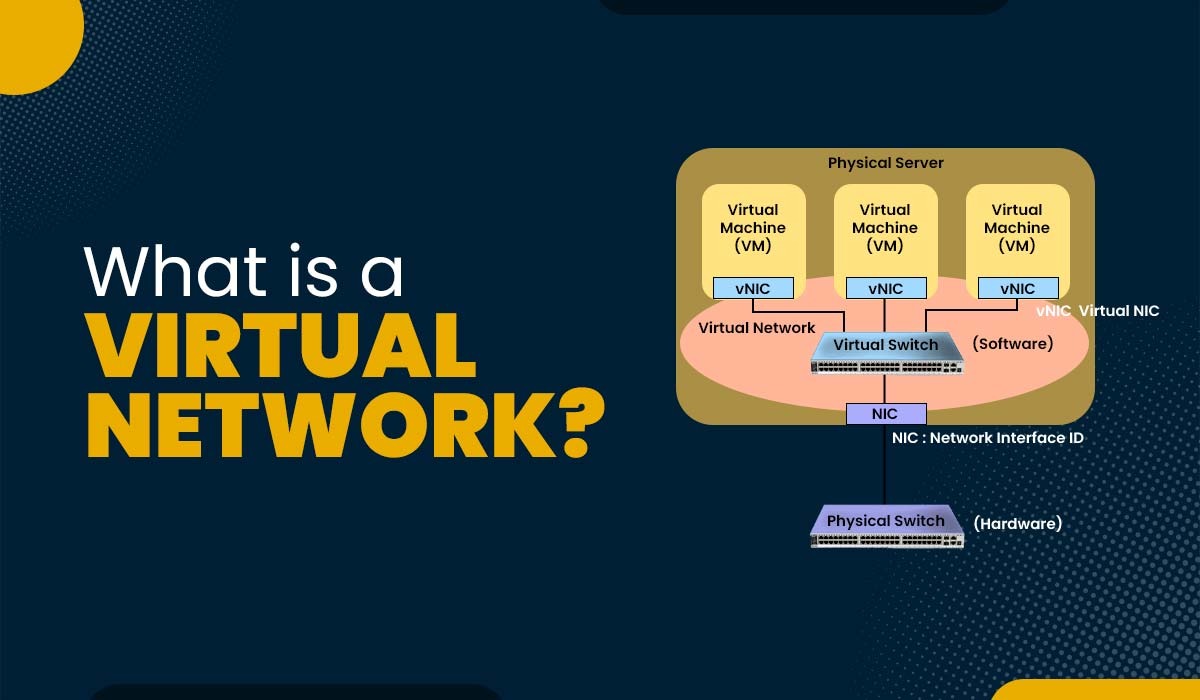
Introduction Virtual networks have gained popularity and significance in the field of computing and communication. They offer users the ability to create and manage networks that are independent of the physical infrastructure, such as routers, switches, cables, and servers. It can also isolate and segment traffic from different sources or destinations based on rules and…
-
What is a Network Switch?
Introduction A Network Switch is a networking device that assist in connecting multiple computers or network devices. They play a significant role in the creation and management of networks as well as enhancing their performance, security, and scalability. By learning about network switches, we get insight about how networks function and how we can optimize…
-
What is ARP Poisoning?

Introduction The Address Resolution Protocol (ARP) is a widely used protocol that enables devices within a LAN to communicate by linking their IP addresses with their MAC addresses. However, this protocol has a flaw as it cannot verify the authenticity of received ARP messages. This vulnerability exposes it to a type of cyberattack called ARP…
-
Transport Layer Protocols
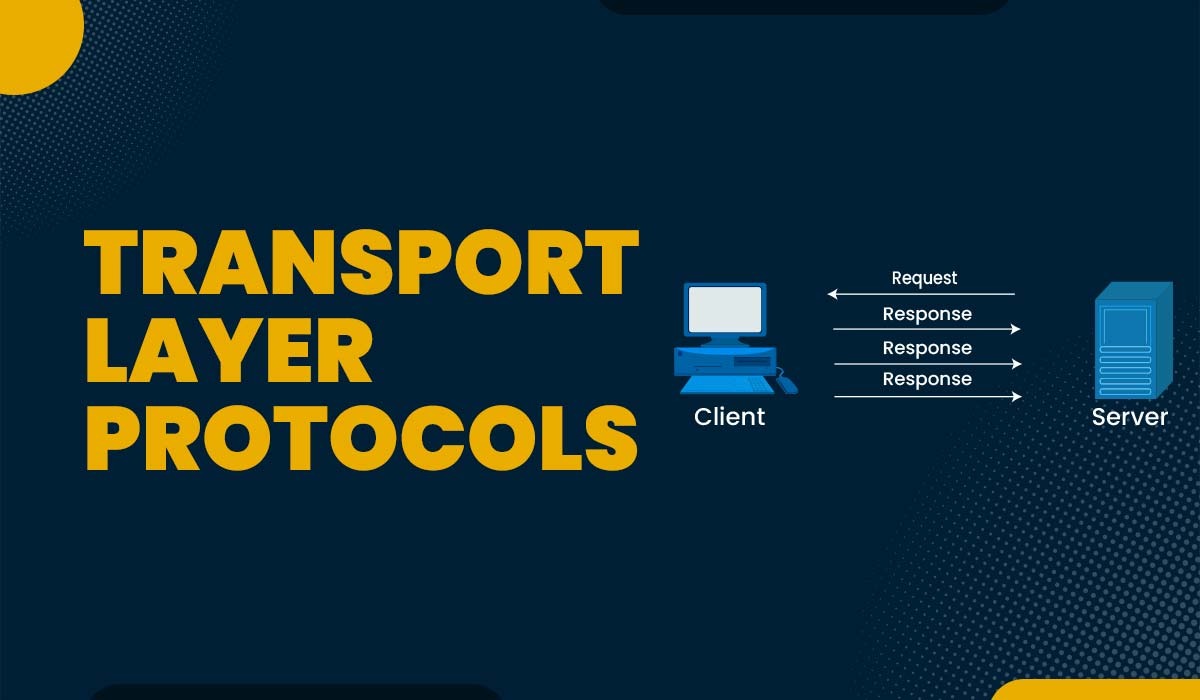
Introduction The transport layer is one of the seven layers of the OSI model, which is a reference framework that explains the process of transmitting data between computers. The OSI model was developed by ISO in 1984 and is now considered as an architectural model for inter-computer communications. Transport layer protocols play a significant role…