-
What are the Different Types of IP Address?

Introduction The Internet has changed the way we communicate, access information, and share data. With the help of the Internet, one can connect with people as well as devices all over the world, regardless of physical distance or location. But the question that arises now is, how do devices identify each other and communicate? The…
-
Objectives of Cyber Security

Introduction As technology advances, so does the reliance of businesses on digital services and networks. We all are either directly or indirectly dependent on the security and integrity of online systems in order to protect personal data as well as business operations. Cybersecurity is of utmost importance nowadays, as we all know that cyberattacks can…
-
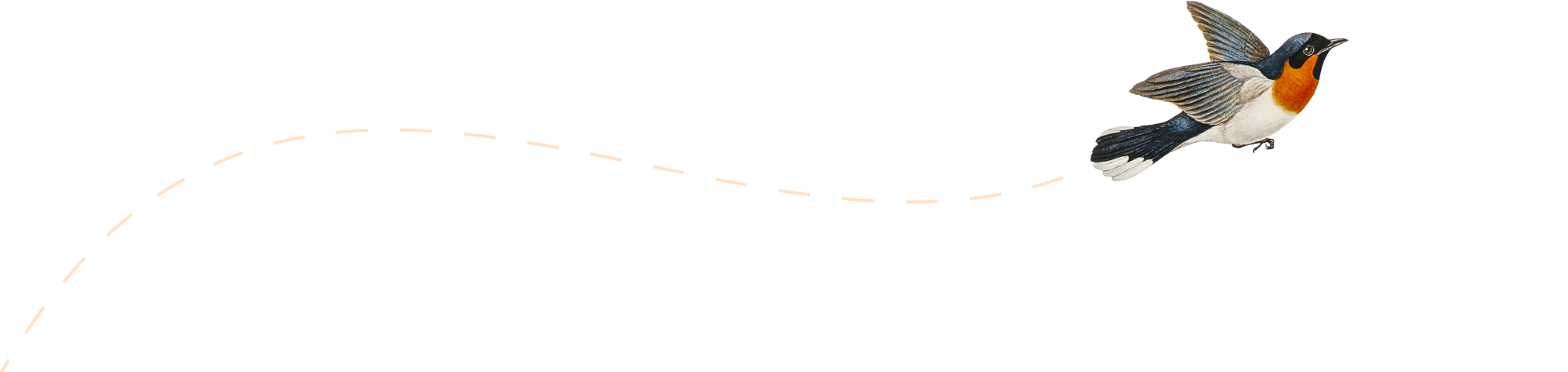
What is IS-IS Protocol?
Introduction IS-IS is a link-state routing protocol that allows the efficient transmission of data in large and complex networks. Now, many network enthusiasts have heard of the term routing protocol, which is a set of rules and algorithms. Routing protocols are utilized by network devices to determine the best path for sending the data between…
-
What are BGP Attributes and its Types?

Introduction Border Gateway Protocol (BGP) is the routing protocol utilized for exchanging network reachability information between AS (Autonomous System) on the Internet. BGP facilitates the advertisement of its own network prefixes by each AS. This allows them to gain knowledge about prefixes of other ASes thereby ensuring end-to-end connectivity across the global network. An essential…
-
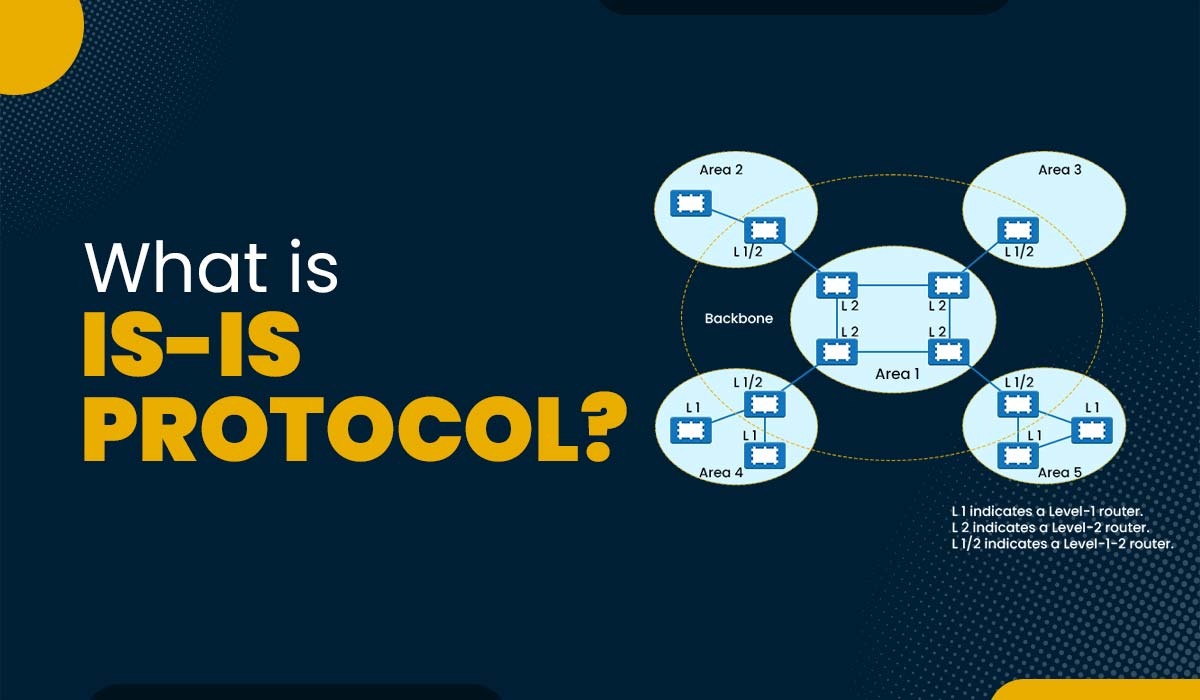
What is Multicast Routing in Computer Networks?
Introduction A wide range of newly developed network applications need packets to be sent from one or more senders to several receivers. These include shared data applications, data feeds (like stock quotes), interactive gaming (like distributed multiplayer games like CSGO), streaming continuous media (like the transfer of the audio, video, and text of a live…
-
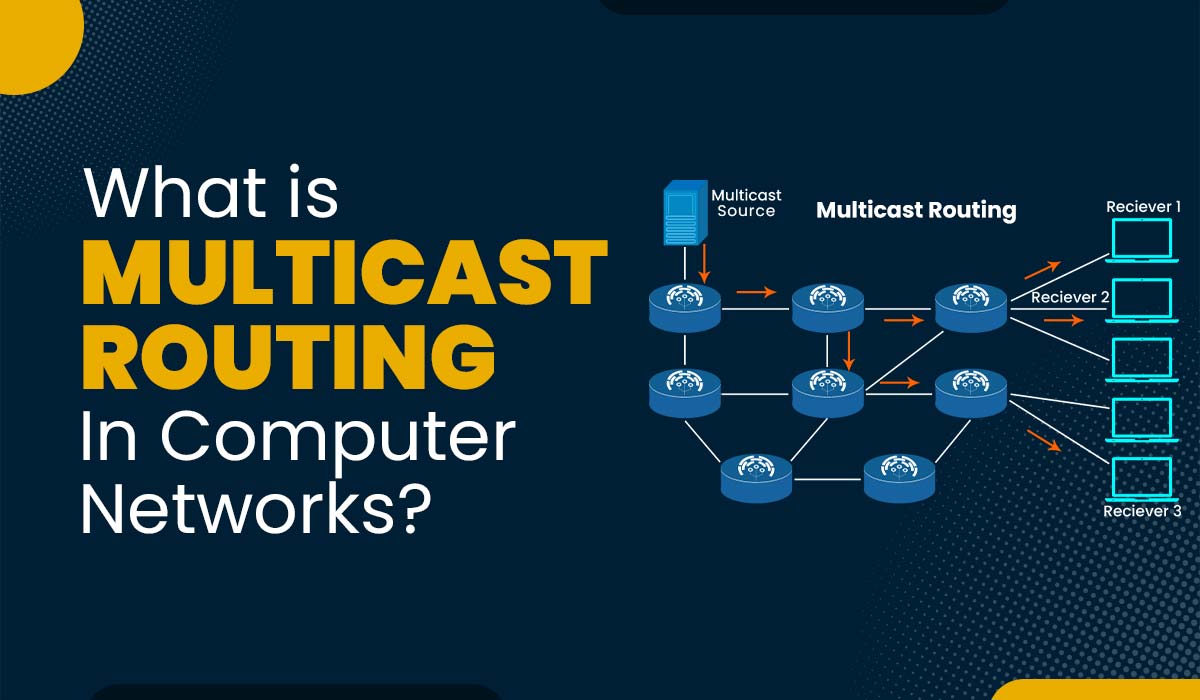
What is Bus Topology in Computer Network? (Updated 2025)
Introduction Computer networks play a vital role in allowing communication, data sharing, and resource utilization across devices. Within these networks, network topologies define how devices are interconnected. Various types of network topologies exist, such as point-to-point, mesh, star, ring, tree, and hybrid. Each topology has its own advantages and disadvantages. In this blog post, we…
-
What is an Access Point in Networking and its Types?

Introduction An access point, also known as AP, serves as a bridge between wireless networks and enables wireless devices to connect. It acts as a gateway that allows internet access and grants users connectivity to network resources. In this blog, we will discuss the topic of “access points”. We will look into its definition, its…
-
What is OSPF Stub Area and its Types?
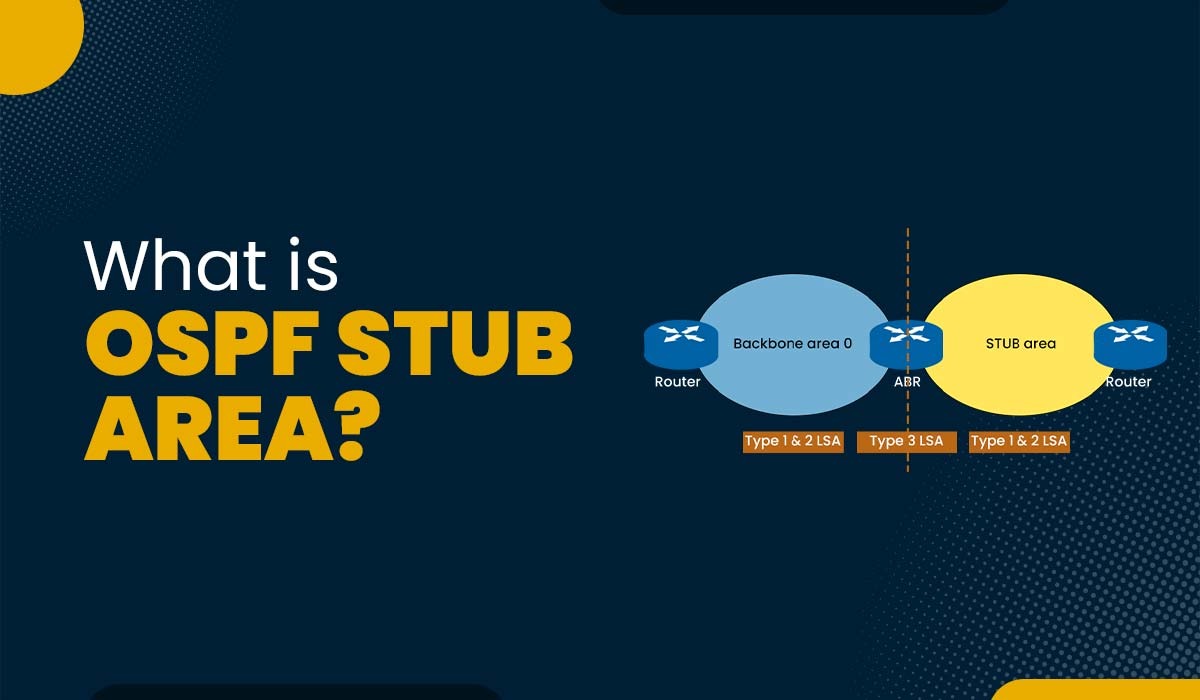
Introduction OSPF, also known as Open Shortest Path First, is a routing protocol that utilizes link state information to determine the efficient paths between routers within a network. OSPF divides networks into units called areas, which are logical groupings of OSPF networks, routers, and links that share the same area identification. One advantage of utilizing…
-
What is Proxy ARP in Networking?
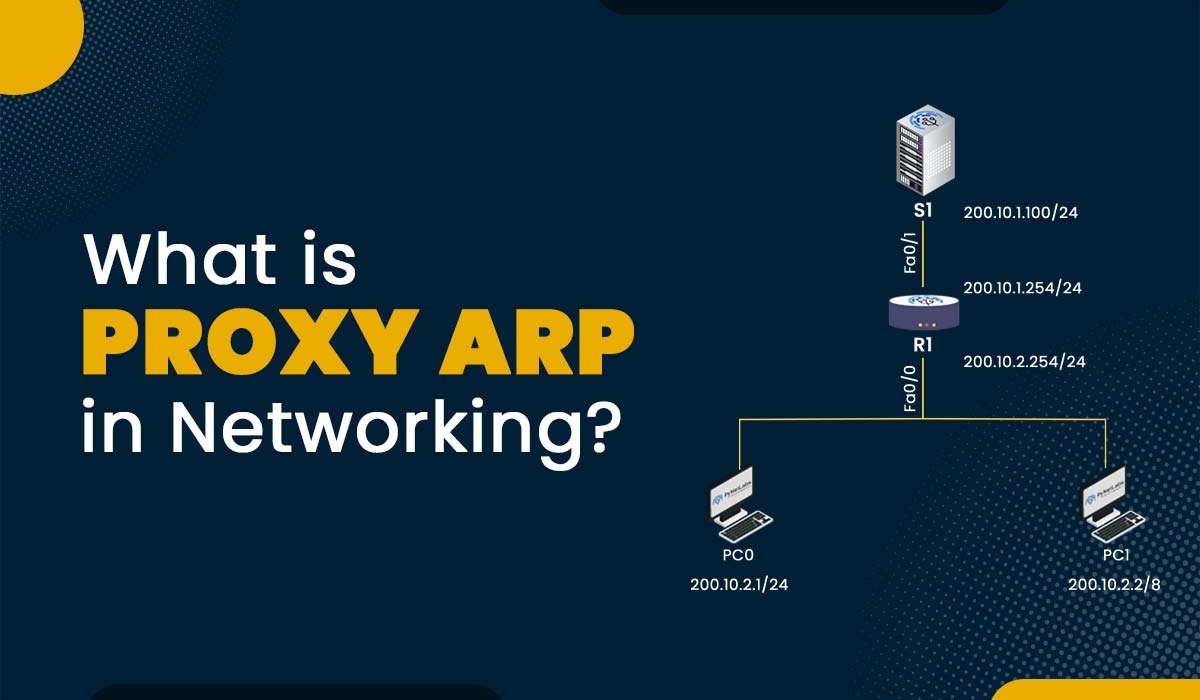
Introduction If Someone is interested in networking, they must have heard the term Proxy ARP. But what does it really mean, and how does it work? Proxy ARP is a technique that allows a device to respond to the ARP requests on behalf of another device. This can be useful in situations where the devices…
-
Is Cyber Security a Good Career?

Introduction Cybersecurity is the method of protecting networks, systems, devices, and information from cyberattacks. It is crucial in the digital world, as cyber threats are continuously evolving, and as a result, it can affect the integrity of data. Cyber security is not only critical for individuals and agencies but also for the nation as a…