Introduction
Multicast is a technique that allows one source to send data to multiple destinations simultaneously without duplicating the data packets. This can save bandwidth and improve network efficiency, especially for applications that involve streaming media, online gaming, video conferencing, or distributed computing. However, multicast routing is a challenging task, as it requires the network devices to maintain information about the multicast groups and their members and to construct optimal paths for delivering the data.
In this blog post, we will learn about PIM protocol, a family of multicast routing protocols, and explain how it operates in different scenarios. Before getting into more details, let’s first understand the PIM routing protocol.
What is the PIM Protocol?
PIM Protocol, which stands for Protocol Independent Multicast, is a multicast routing protocol used in computer networks to route data packets to multiple recipients efficiently. It is an adaptive and scalable protocol that supports multicast routing on a variety of network topologies, including LANs, WANs, and the Internet.
PIM is called protocol-independent because it does not depend on any specific unicast routing protocol for topology discovery. Instead, it uses the existing unicast routing table to perform reverse path forwarding (RPF) checks, which prevent loops and flooding in the network. RPF checks to ensure that a multicast packet is forwarded only if it arrives on the interface with the shortest path to the packet’s source.
PIM Protocol is not a single protocol but a collection of protocols that operate in different modes:
- PIM Sparse Mode (PIM-SM)
- PIM Dense Mode (PIM-DM)
- PIM Bidirectional (Bidir-PIM)
- PIM Source-Specific Multicast (PIM-SSM)
Now that we have a basic understanding of PIM routing protocol, let’s discuss its functioning.
How Does PIM Protocol Works?
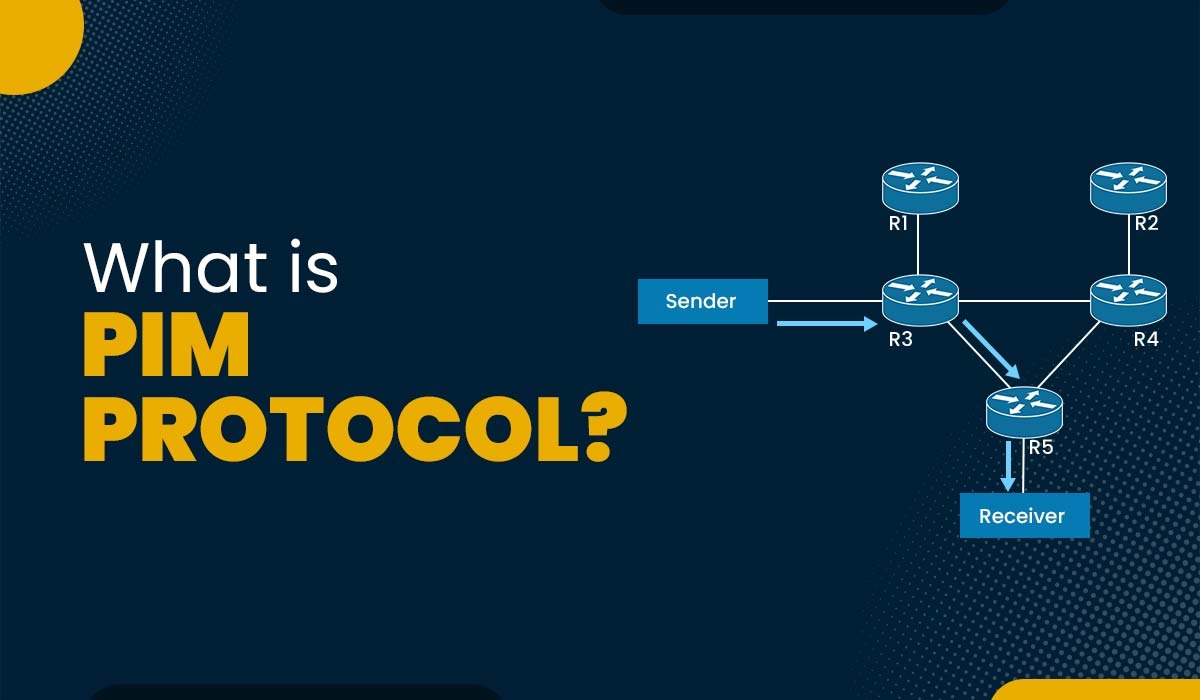
PIM Protocol works by building distribution trees or multicast routing trees that connect the sources and the receivers of a multicast group. A distribution tree is a path through the network used to deliver multicast data. There are two types of distribution trees: source trees and shared trees.
Source Tree
A source tree is a tree that has its root at the source of the multicast data. It represents the shortest path from the source to each receiver and thus minimizes the latency in the network. However, it also requires more state information to be maintained by the routers, as they need to know the addresses of all sources for each group.
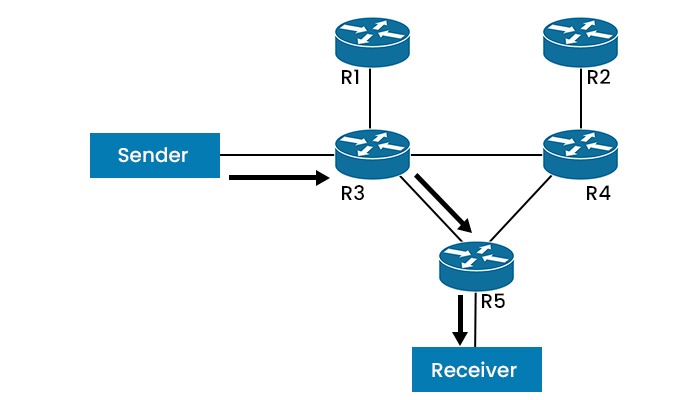
Shared Tree
A shared tree is a tree that has its root at a common point, called a rendezvous point (RP). It does not depend on the location of the sources or the receivers and thus reduces the state information required by the routers. However, it may not provide the optimal path for data delivery, as it may introduce extra hops or detours.
PIM is a protocol that allows devices to receive multicast data from specific groups. It works in three steps:
- Multicast group joining: A device that wants to get data from a group sends a message to nearby routers, saying, “I want to join this group.”
- Multicast tree building: Routers use PIM Protocol to decide the best way to send multicast data from the sender to the receiver. This creates a multicast tree.
- Data delivery: After the multicast tree is built, data can flow along the tree from the source (sender) to the destination (receiver). This avoids sending data to the whole network and saves bandwidth. PIM has different modes of operation.
Note: PIM Protocol uses both types of trees in different modes. In PIM-SM and PIM-SSM, routers can switch between source trees and shared trees dynamically, depending on the traffic pattern and network conditions. In PIM-DM and Bidir-PIM, routers only use source trees or shared trees respectively.
Let’s now discuss the different modes of PIM protocol.
Types of PIM Protocol
In this section, we will briefly describe each PIM protocol and how it operates.
1. PIM Dense Mode
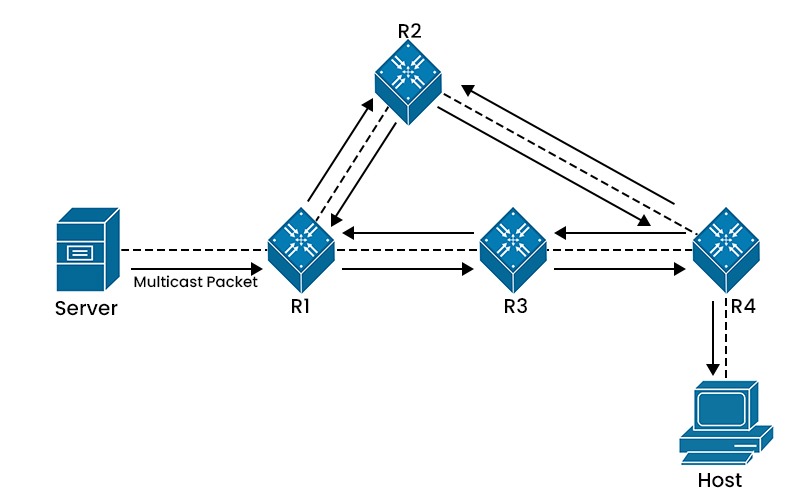
PIM Dense Mode (PIM-DM) is a protocol that uses dense multicast routing. It assumes that most nodes in the network are interested in receiving multicast data from any source. It implicitly builds source trees by flooding multicast traffic domain-wide and then pruning back branches of the tree where no receivers are present. This way, it can quickly establish multicast forwarding without requiring any prior knowledge of the sources or the receivers.
For example, if a company’s internal network wants to broadcast live video conference signals to offices across the company, it can use PIM-DM. Since most offices need this service, PIM-DM sends the message everywhere and then cuts off the unnecessary parts to optimize delivery. Below, we have shown it with the help of an image.
2. PIM Sparse Mode
PIM Sparse Mode (PIM-SM) is a protocol that uses sparse multicast routing. It assumes that only a few nodes in the network are interested in receiving multicast data from any source. It explicitly builds unidirectional shared trees rooted at a rendezvous point (RP) per group and optionally creates shortest-path trees per source. This way, it can avoid sending data to nodes that do not want it and reduce the state information required by the routers.
PIM-SM operates in two phases: join and prune. In the join phase, routers that have receivers for a multicast group send join messages to the RP to indicate their interest in receiving data. The RP then discovers the sources for the group and forwards the data to the joined routers along the shared tree. In the pruning phase, routers that do not have receivers for a multicast group send prune messages to the RP to indicate their disinterest in receiving data. The RP then stops forwarding the data to the pruned routers.
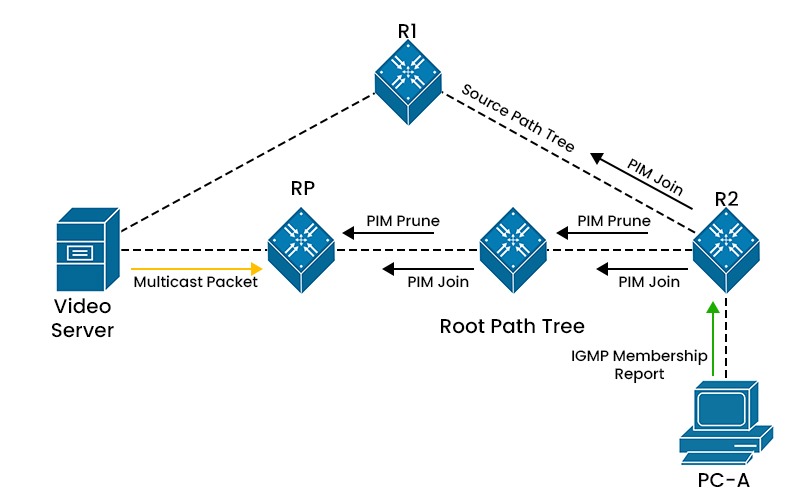
PIM-SM also allows routers to switch from the shared tree to a source tree if they want to receive data from a specific source more efficiently. This is done by sending join messages to the source and pruning messages to the RP. This process is called source-specific join or shortest-path tree (SPT) switchover.
Note: PIM-SM generally scales well for wide-area and inter-domain networks, where multicast groups are sparse and sources are distributed.
3. Bidirectional PIM
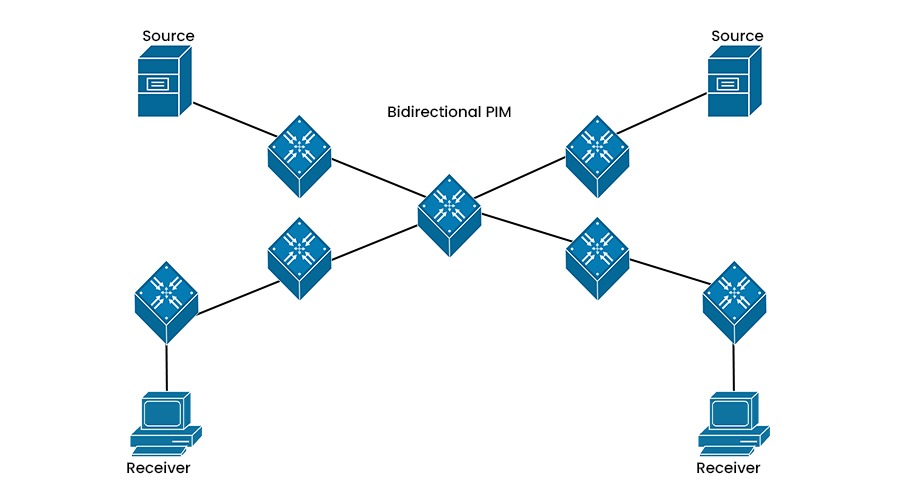
Bidirectional PIM (Bidir-PIM) is a protocol that explicitly builds shared bidirectional trees. It does not use source-specific state or RPF checks and thus simplifies multicast routing. It never builds a shortest-path tree so that it may have longer end-to-end delays than PIM-SM, but it scales well because it needs no source-specific state.
Bidir-PIM operates in a similar way as PIM-SM, except that it uses a designated forwarder (DF) election mechanism to select one router per link to forward data on the shared tree. The DF is responsible for sending data from the sources on the link to the RP and receiving data from the RP to the receivers on the link. The DF election is based on the unicast routing metrics and the priority of the routers.
Bidir-PIM is suitable for applications that involve many-to-many communication, such as video conferencing or collaborative work.
4. PIM Source-Specific Multicast
PIM Source-Specific Multicast (PIM-SSM) is a variant of PIM-SM that builds trees that are rooted in just one source per group. It offers a more secure and scalable model for a limited number of applications, mostly broadcasting of content. In SSM, an IP datagram is transmitted by a source to an SSM destination address, and receivers can receive this datagram by subscribing to the channel.
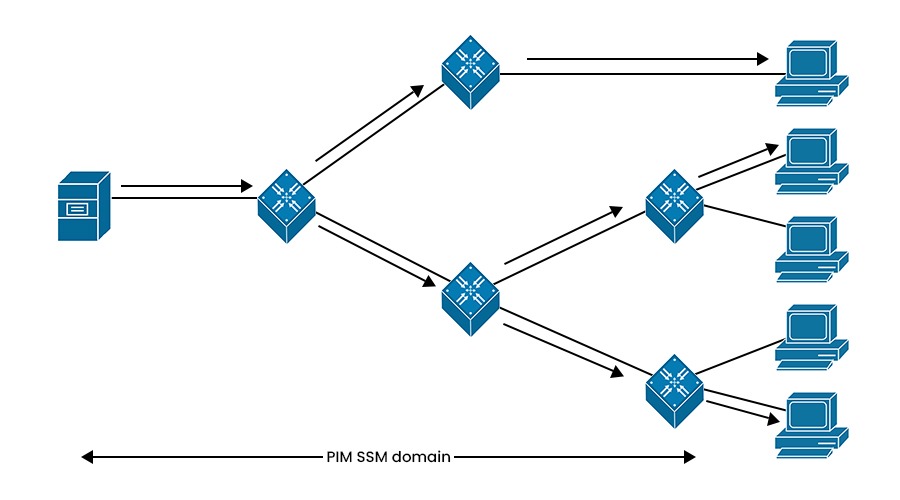
PIM-SSM operates in a similar way as PIM-SM, except that it does not use an RP or a shared tree. Instead, it uses IGMPv3 or MLDv2 to allow receivers to specify the source address when joining a group. It then builds a source tree from the source to each receiver using join messages.
These are the different PIM Protocols.
PIM vs Other Multicast Routing Protocols
As with any other routing protocol, PIM also possesses its limitations relating to its scope of application. Other protocols perform the dame functions, but PIM has its own benefits as a result of its flexibility and separation from unicast routing protocols.
| Feature | PIM Protocol | DVMRP | MOSPF | IGMP |
|---|---|---|---|---|
| Full Form | Protocol-independent multicast | Distance Vector Multicast Routing Protocol | Multicast Open Shortest Path First | Internet Group Management Protocol |
| Description | Multicast routing protocol used in computer networks | Uses distance vector routing | Extension of OSPF for multicast | Manages host membership in multicast groups |
| Strengths | Works with any unicast routing protocol | Simple and widely supported | Integrated with OSPF | Works at the host level |
| Weaknesses | Can be complex to configure | Not scalable for large networks | High processing overhead | Requires a multicast routing protocol like PIM |
To facilitate the development of new multicast applications, PIM is the most suitable option because of its ability to operate with different unicast routing protocols.
Components of PIM Protocol
Here are the Components of PIM Protocol:
1. Rendezvous Point (RP)
RP is a central point for all PIM-SM multicast group registrations and it helps in the efficient administration of multicast traffic load balancing. It could be manually configured or dynamically elected.
2. Multicast Distribution Tree (MDT)
It determines the route taken by multicast packets from the sender to receivers. It has 2 varieties: Shortest Path Tree (SPT) and Shared Tree (RP-based).
3. Reverse Path Forwarding (RPF)
It verifies that multicast packets travel along the proper path, preventing loops. RPF makes use of unicast routing tables to find the best path.
Applications of PIM in Real-World Scenarios
PIM is common in real world networking infrastructure that require the use of multiple streams of data.
- IPTV and Video Streaming: PIM Protocol delivers live video streams to numerous users effectively. It decreases the bandwidth consumption compared to unicast streaming.
- Financial Market Data Distribution: Data from the stock market is sent simultaneously to numerous financial institutions in real-time. PIM assures the rapid and dependable delivery of data.
- Corporate Multicast Applications: PIM handles video conference calls, and corporate virtual meetings.
Advantages of PIM Protocol
Some advantages of PIM Protocol:
- Some protocols utilize unicast routing independent of PIM, such as OSPF, EIGRP, BGP, and RIP.
- It sends one stream of data to various end users, thus reducing network traffic.
- With PIM, multicast allows one stream to be sent to numerous recipients as opposed to multiple unicast streams, lowering the processing requirements.
- Applicable in IPTV, live broadcasts, corporate communication, speech or video conferences, and financial data distribution.
Disadvantages of PIM Protocol
- Setup of Rendezvous Points, multicast groups, and routing tables needs to be on point.
- PIM multicasting can be made ineffective due to poor configurations.
- It can be targeted by multicast spoofing and DoS attacks without proper protection.
- Multicast routing is more complex than unicast since it involves extra components such as RPF (Reverse Path Forwarding), RP, and multicast trees.
Frequently Asked Questions
Q1. What is the difference between IGMP and PIM?
Both IGMP and PIM work together for multicast delivery. The main difference between the two is that, in the case of IGMP, it is used by hosts to join multicast groups, whereas PIM is mainly used by routers to build multicast trees.
Q2. What are 3 modes in which PIM can operate?
The three modes in which PM can operate are:
- PIM Sparse Mode (PIM-SM)
- PIM Dense Mode (PIM-DM)
- PIM Bidirectional (Bidir-PIM)
Q3. What is the PIM mechanism?
The PIM mechanism is a way of routing multicast data over IP networks. It uses other routing protocols to discover the network topology and builds multicast trees based on the receivers’ interests.
Q4. What is a PIM in computer?
PIM in computer stands for Processing In Memory, which is a process that allows computations and processing to be performed within a computer’s memory module.
Conclusion
PIM is a crucial multicast routing protocol that enhances the efficiency of data distribution in modern networks. In this blog post, we have explained PIM protocol, a family of multicast routing protocols. We have explained how PIM operates in different modes: PIM Dense Mode, PIM Sparse Mode, Bidirectional PIM, and PIM Source-Specific Multicast.
If you have any questions or feedback, please feel free to leave a comment below.