Introduction
In 1981, the Routing Information Protocol (RIP) was first developed as GWINFO in the Xerox Network Systems (XNS) protocol suite for the Xerox PARC Universal Protocol. RIP, which was first described in RFC 1058 in 1988, has a reputation for being simple to set up and use on small networks.
It is an Interior Gateway Protocol (IGP) designed to distribute routing information within an Autonomous System (AS). RIP Protocol is an integral part of PyNet Labs’ CCNA Training.
What is RIP Protocol in Computer Networks?
RIP Protocol or Routing Information Protocol is a dynamic routing protocol that uses hop count as a routing metric to find the best route between a source network and a destination network. It is a distance-vector routing protocol that operates at the Network layer of the OSI model and has an AD value of 120. The 520 port is used by RIP.
- It is an open-standard protocol and not a Cisco Proprietary Protocol.
- It is one of the oldest and simplest routing protocols in existence.
- RIP uses hop count as the metric to determine the best path to a destination network.
- Each router maintains a routing table containing entries for reachable networks and the number of hops required to reach them.
- Routers periodically broadcast their routing tables to neighboring routers, allowing them to update their own tables accordingly.
- This process continues until convergence is achieved, meaning all routers have learned the complete network topology.
One notable characteristic of RIP is its limitation of supporting networks with a maximum hop count of 15. If a network is more than 15 hops away, it is considered unreachable by RIP. This is why, it is preferable for smaller networks.
While RIP was widely used in the past, it has gradually been replaced by more advanced and scalable routing protocols such as Open Shortest Path First (OSPF) and Border Gateway Protocol (BGP). However, RIP Protocol still finds its application in certain scenarios where simplicity and ease of configuration are prioritized over scalability and performance.
How Routing Information Protocol Works?
In order to choose which path to place a packet on to reach its destination, RIP uses a distance vector method. A routing table, or a list of all the locations the router is capable of reaching, is kept by each RIP router. Every 30 seconds, each router broadcasts its whole routing table to the closest neighbours.
The other routers to which a router is directly connected in this sense are the other routers that are on the same network segments as the chosen router. Up until all RIP hosts inside the network are aware of the same routing paths, the neighbours send the information on to their closest neighbours in turn. This shared knowledge is called convergence.
A router will update its table entry with the length and next-hop address of the shorter path if it receives an update on a route and the new path is shorter. If the new path is longer, it will wait for a “hold-down” period to check if subsequent updates also include the longer path. If the new, lengthier path is found to be stable, it will just update the table entry.
The network learns about a router crash or broken network connection when the affected router stops delivering updates to its neighbours or ceases sending and receiving updates across the broken connection. A RIP router will remove a particular route and notify the rest of the network of the issue through its own periodic updates if the routing database for that route isn’t updated six times in a row (or for 180 seconds).
Features of Routing Information Protocol
Here are some features of the Routing Information Protocol:
- The network exchanges updates on a regular basis.
- Routing information updates are sent continuously.
- Updates include full routing tables.
- Routers always trust routing data obtained from neighbor routers. It’s also referred to as “routing on rumors.”
RIP Protocol Versions
There are three versions of RIP – RIPv1, RIPv2, and RIPng. Let’s discuss each one by one.
RIP Version 1 (RIPv1):
RIPv1 is defined in RFC 1058 as a fundamental protocol that works with small IPv4 networks. The IP address 255.255.255.255 receives routing updates broadcast from RIPv1 every 30 seconds, while the entire routing table is shared. The protocol maintains a hop count limit of 15. RIPv1 operates as a classful protocol, which does not distribute subnet mask details, and it automatically assumes default masks for IP classes (e.g., /8 for Class A).
RIPv1 provides no authentication methods, making it vulnerable to unauthorized update threats. Network bandwidth becomes inefficient because this protocol lacks both multicast capability and Variable-Length Subnet Masking (VLSM) features for bigger networks.
RIP Version 2 (RIPv2):
RIPv2 is defined in RFC 2453, and it provides RIPv1 network enhancements for medium-sized IPv4 networks. VLSM and CIDR become possible through RIPv2 since it includes subnet masks in its updates for classless routing. RIPv2 uses the multicast address 224.0.0.9 for updates, reducing network traffic compared to RIPv1’s broadcasts. It adds MD5 authentication to secure routing exchanges. RIPv2 also supports route tags for filtering and redistributing routes. Updates are more efficient, as they can send only changes instead of full tables, improving performance in dynamic networks.
RIP Next Generation (RIPng):
RIPng, defined in RFC 2080, is designed for IPv6 networks. It adapts RIPv1 and RIPv2 features for the 128-bit address space of IPv6. Like its predecessors, it uses a 15-hop limit and sends updates every 30 seconds via multicast to FF02::9. RIPng supports classless routing and includes subnet information for flexible network designs. It retains MD5 authentication for security and supports route tags. The network protocol RIPng functions through UDP port 521 to supply enhanced capabilities for modern networks that support large address blocks while keeping the simplicity of standard RIP functions. It’s ideal for IPv6-only or dual-stack environments.
| RIPv1 | RIPv2 | RIPng |
|---|---|---|
| Updates are sent as Broadcast | Updates are sent as Multicast | Updates are sent as Multicast |
| Broadcast at 255.255.255.255 | Multicast at 224.0.0.9 | Multicast at FF02::9 |
| Authentication is not supported | It supports Authentication | Does not support authentication by itself. |
| Classful | Classless | Classless |
Classful Routing Protocol doesn’t send information on subnet mask in its routing updates, whereas on the other hand, Classless Routing Protocol sends information on subnet mask in its routing updates.
Routing Information Protocol Message Format
The RIP message format allows information to be transmitted to all different routers. The message below contains the following fields that are included in RIP:
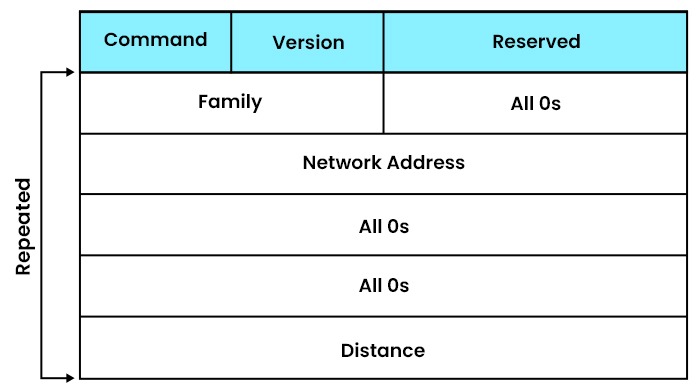
- Command: Command is an 8-bit field that allows a request or reply. The request value is 1, and the reply value is 2.
- Version: It defines the protocol version we are using. For example, if we are using version 1 of the protocol, then in this field, we set 1.
- Reserved: It is the reserved field, so zeros are placed in this area.
- Family: Family is a 16-bit field. It means that if the TCP/IP family is used, then the value 2 is entered in this field.
- Network Address: It is a 14-byte field. For example, if the IPv4 version is being used, 4 bytes are being used, and the other 10 bytes are all zeros.
- Distance: It specifies the hop count, which means the number of hops allowed to reach the destination.
Let’s learn a little more about the metric of RIP.
Hop Count
Hop Count is the number of routers between the source and destination networks. The routing table includes the path that has the lowest hops since it is considered to be the best way to connect to a network. By limiting the number of hops permitted between a source and a destination, RIP avoids routing loops. A maximum of 15 hops are allowed in RIP.
Let’s try to configure a small lab by advertising the Networks using:
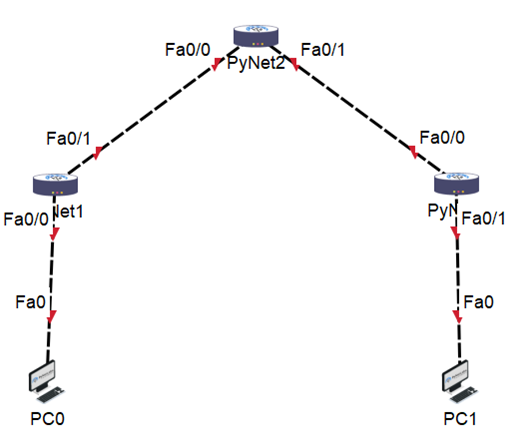
Consider the 3-router topology shown above (PyNet1, PyNet2, PyNet3). PyNet1 ‘s IP addresses are 192.168.1.1/24 on fa0/0 and 12.10.1.1/30 on fa0/1. PyNet2’s IP addresses are 12.10.1.2/30 on fa0/0 and 12.10.2.2/30 on fa0/0. PyNet3 has the following IP addresses: 12.10.2.1/30 on fa0/0, 192.168.2.1/24 on fa0/1.
Configure RIP for PyNet1:
R1(config)# router rip
R1(config-router)# network 192.168.1.0
R1(config-router)# network 12.10.1.0
R1(config-router)# version 2
R1(config-router)# no auto-summary
Configuring RIP for PyNet2:
R2(config)# router rip
R2(config-router)# network 12.10.1.0
R2(config-router)# network 12.10.2.0
R2(config-router)# version 2
R2(config-router)# no auto-summary
Similarly, Configure RIP for PyNet3:
R3(config)# router rip
R3(config-router)# network 12.10.2.0
R3(config-router)# network 192.168.2.0
R3(config-router)# version 2
R3(config-router)# no auto-summary
Note: There is no auto-summarisation command that disables the auto-summarisation.
RIP Timers and Their Roles
Timers in RIP aid in controlling performance. There are 4 types of timers related to RIP.
Update Timer
The routers using RIP typically communicate routing information every 30 seconds by default. The routers periodically swap over their routing tables using an Update timer.
Invalid Timer
When 180 seconds have passed without an update, the destination router deems it invalid. The destination router’s mark hop counts as 16 for that router in this instance.
Hold down Timer
The router waits for a neighbouring router to respond during this period. The router is deemed dead if it is unable to reply within a predetermined period of time, which is 180 seconds by default.
Flush Time
If a route doesn’t respond in the flush time, its entry will be flushed. It is 60 seconds by default.
Routing Information Protocol Configuration
At the OSI model application layer, RIP (Routing Information Protocol) is executed and the process of configuration of RIP is very easy. When the computers and interfaces of the router receive IP addresses, the router RIP command is issued by the developers, then inform the router to enable RIP. After that, the developer uses the network command so that users can analyze the networks they want to work with and only need to specify the networks directly connected to the router.
Users can also configure any port to run the following actions:
- Stop RIP packets from being shared or received.
- Receive packets in multiple formats.
- Shared packets are presented to the RIPv1 broadcast address for each different RIP version.
Security Concerns of RIP
Some of the notable security concerns of RIP are:
- Routing Table Spoofing: Routing table spoofing remains a significant security threat with RIP. This is normally so when a malicious router on the network sends the wrong routing update to the other routers in the network. This can lead to rather unstable and possible routing loops and thus allows the attacker to redirect traffic to unauthorized or compromised equipment.
- Sniffing and Eavesdropping: Sniffing and eavesdropping are also some of the issues affecting RIP security. Since RIP updates are sent in plain text, they are unsecured and can be easily interpreted by any unauthorized party. This enables an attacker to ascertain the topology of a network which they can use to proceed to launch more attacks.
- Denial of Service (DoS) Attacks: Another security threat to RIP networks, is the DoS or denial of service attacks. A malicious router can flood false routing updates that other routers in the network will interpret as fresh; this would result in congestion and instability. This can collapse the network or certain routers and resulting in a loss of service.
- Lack of Authentication and Authorization: Perhaps the most important criticism that can be pointed to the RIP is that the protocol does not provide the means for authentication and authorization. This enables the unauthorized router to become involved in routing functions hence exposing the network to other dangers such as unauthorized access and penetration.
Advantages of RIP Protocol
Below, we have discussed some of the advantages of RIP protocol.
- Easy to Configure
• Simple setup with minimal parameters required
• Easy to implement and manage
• Reduces deployment time and effort - Less Complexity
• Uses simple distance-vector routing algorithm
• Limited functionality reduces management overhead
• Easier to troubleshoot and maintain - Less CPU Utilization
• Lightweight operations reduce CPU load
• Suitable for networks with devices that have limited processing power
• Efficient use of resources - Easy to Understand
• Straightforward and intuitive concepts
• Use of hop count as primary routing metric is simple and transparent
• Easy to comprehend and manage - Promotes Load Balancing
• Treats routes with the same hop count as equal-cost paths
• Distributes network traffic more evenly
• Improves overall network performance and resilience - Loop-Free
• Prevents routing loops by limiting maximum hop count to 15
• Reduces risk of network instability
• Contributes to overall network stability and reliability
Disadvantages of RIP Protocol
Below, we have discussed some of the disadvantages of the RIP protocol.
- Limited Scalability:
• Limited to 15 hops, making it unsuitable for large networks
• Can’t support networks with many routers and subnets
• Not scalable for modern networks - Slow Convergence:
• Updates every 30 seconds, causing slow convergence
• Routers may take minutes to detect changes
• Can lead to network instability and black holes - High Network Overhead:
• Sends routing updates periodically, wasting bandwidth
• Can cause network congestion and packet loss
• Inefficient use of network resources - Lack of Support for Modern Features:
• No support for modern features like authentication and encryption
• No support for MPLS, VPN, or IPv6
• Limited functionality compared to modern routing protocols.
As a result of these limitations, RIP is less commonly used in modern network environments, where more scalable and feature-rich routing protocols like OSPF and BGP are preferred. Now, the question is –
Why is RIP Dead?
- It is only based on hop count. So, if there is a better route available with better bandwidth, it will not select that route.
- RIP uses a lot of bandwidth because it sends updates every 30 seconds.
- Only 15 hop counts are supported by RIP; hence a maximum of 16 routers can be specified.
- The convergence rate of RIP is very low, which means if a link goes down, it will take a lot of time to find an alternate route.
These are a few reasons why we prefer using other Routing Protocols like EIGRP and OSPF instead of Routing Information Protocol.
Frequently Asked Questions
Q1. What is routing information protocol in networking?
Routing Information Protocol (RIP) is a dynamic routing protocol used in computer networks to facilitate the exchange of routing information between routers. It is one of the oldest and simplest routing protocols in existence.
Q2. What are the 3 types of routing protocols?
The three types of routing protocols are distance-vector protocols, link-state protocols, and hybrid protocols. The choice of routing protocol depends on factors such as network size, complexity, scalability requirements, and administrative preferences.
Q3. What is the RIP protocol based on?
The RIP protocol is based on the distance-vector algorithm, which determines the best path to a destination network based on the distance or metric associated with each route. It operates by exchanging routing information between routers, allowing them to update their routing tables accordingly.
Q4. Why use routing information protocol?
Routing Information Protocol (RIP) is used for its simplicity, compatibility with various devices and operating systems, and the ability to provide basic routing functionality in small networks.
Conclusion
In this blog, we have explained what is Routing Information Protocol in computer networks, how it works, what are its various versions and other things related to RIP Protocol. Routing Information Protocol (RIP) is outdated and is not mostly used. There are other protocols that replaced it, and you can learn about all these advanced protocols in our CCNA training.